From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Wanted: SHARE Volume I proceedings Newsgroups: bit.listserv.ibm-main Date: Mon, 14 Sep 2009 09:25:48 -0400BShannon@ROCKETSOFTWARE.COM (Bob Shannon) writes:
post from earlier this year
https://www.garlic.com/~lynn/2009.html#47
https://www.garlic.com/~lynn/2009.html#70
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: IT Story New Standard For EU-Compliant Electronic Signatures Date: 14 Sep, 2009 Blog: Information Security NetworkIT Story New Standard For EU-Compliant Electronic Signatures
from above:
The standard defines a series of profiles for PAdES -- Advanced
Electronic Signatures for PDF documents -- that meet the
requirements of the European Directive on a Community framework for
electronic signatures (Directive 1999/93/EC).
... snip ...
also
New ETSI standard for EU-compliant electronic signatures
http://www.net-security.org/secworld.php?id=8070
... note ... a decade ago, we had been brought in to help word-smith the cal. state electronic signature legislation. One of the issues was that there was significant lobbying by certain interests to effectively use off-the-shelf digital signature technology.
The lawyers pointed out that off-the-shelf digital signature technology was effectively authentication ... but didn't meet the requirement for "human signature" demonstrating intent, having read, understood, agrees, approves, and/or authorizes.
Conjecture was possible cognitive dissonance (&/or semantic confusion) with the terms "digital signature" and "human signature" both containing the word "signature".
misc. past posts mentioning signatures
https://www.garlic.com/~lynn/subpubkey.html#signature
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Smart Card Alliance slams end-to-end encryption Date: 14 Sep, 2009 Blog: Information Security Networksomewhat followup
Smart Card Alliance slams end-to-end encryption
http://www.finextra.com/fullstory.asp?id=20488
from above:
The US payments industry should use contactless chip cards along with
dynamic cryptograms - rather than end-to-end data encryption - in the
fight against fraudsters, according to an industry association.
... snip ...
in the mid-90s, we had been invited to participate in the x9a10
financial standard working group which had been given the requirement
to preserve the integrity of the financial infrastructure for all
retail payments (i.e. all kinds, debit, credit, ach, stored-value; all
environments, point-of-sale, internet, face-to-face, unattended,
... aka *ALL*). as mentioned the result was x9.59 financial standard
transaction protocol.
https://www.garlic.com/~lynn/x959.html#x959
one of the issues raised in the period was the significant cost of chips being selected for some alternative POS payment specifications ... so an issue was to address what were all the costs. there was also a request from the transit industry to be able to perform secure operation contactless and within the power and elapsed-time requirements of high-traffic transit turnstyle.
part of the cost was addition of "crypto" processor. the issue was that the crypto selected was enormously computationally intensive ... and took significant elapsed time at point-of-sale. the "crypto" processor was to significantly increase the number of circuits ... to effectively perform more of the computations in parallel ... still took a long time ... but also drove up the power requirements (compressing time for power used by all those circuits in smaller time).
an alternative was to change the crypto ... to something with at least equal integrity and security, but significantly lower computational (power & elapsed time) requirements. as previously mention got cost down to something under that of stamp/mailing .... so the next step was looking at paradigm changes to eliminate requirement to mail something.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Hacker charges also an indictment on PCI, expert says Date: 14 Sep, 2009 Blog: Pament Systems Networkre:
There is security proportional to risk ... while it may be impossible to provide one hundred percent security .... but it is possible to eliminate the majority of the existing vulnerabilities and significantly raise the bar ... one scenario is the bar is high enough that the effort to compromise makes it more costly (to the crooks) than the expected (fraudulent) benefit.
many of the existing computer environment vulnerabilities were well
understood 15-20 yrs ago ... and the EU FINREAD standard (a decade
ago) represented countermeasure to significant percentage of those
vulnerabilities.
https://www.garlic.com/~lynn/subintegrity.html#finread
computer environments don't need to have those securities ... I did a
lot of work in the area as undergraduate in the 60s ... but didn't
hear about some of these customers until much later:
https://web.archive.org/web/20090117083033/http://www.nsa.gov/research/selinux/list-archive/0409/8362.shtml
somewhat related thread in this news items ... also archived
here:
https://www.garlic.com/~lynn/2009m.html#86 Voltage SecureData Now Provides Distributed End-to-End Encryption of Sensitive Data
https://www.garlic.com/~lynn/2009n.html#2 Smart Card Alliance slams end-to-end encryption
I mentioned earlier in this thread that in the mid-90s, there was various presentations at banking conferences regarding big motivation of moving the old-style (consumer) dial-up banking to the internet (eliminate the enormous consumer support costs associated with serial-port devices, large library of software, attempting to have some collection that would work on reasonable set of customer PCs) ... basically offloading a bunch of those costs to ISPs.
At the same time, the dialup online commerical/cash-management operations were making presentations that they would never move to the internet because of the significant security issues. Some of this was that the PCs grew up from stand-alone &/or at least non-hostile environment and had few countermeasures to the extremely hostile environment being connected to the internet (where everybody is potential advisery).
That security landscape has changed little in the intervening 15 yrs.
Jim and I had worked together in the 70s and he tried to palm off a bunch of stuff on me when he left for tandem.
Jim
https://www.garlic.com/~lynn/2008p.html#27 Father of Financial Dataprocessing
and I did this "Dependability in Real Life" ... for a NASA dependable
computing workshop (early part of this decade)
https://web.archive.org/web/20011004023230/http://www.hdcc.cs.cmu.edu/may01/index.html
Then a few years ago, he badgered me into interviewing for chief
security architect in redmond ... the interview went on for a few
weeks ... but we weren't able to come to agreement ... some recent
references:
https://www.garlic.com/~lynn/2009.html#60 The 25 Most Dangerous Programming Errors
https://www.garlic.com/~lynn/2009g.html#18 Top 10 Cybersecurity Threats for 2009, will they cause creation of highly-secure Corporate-wide Intranets?
https://www.garlic.com/~lynn/2009h.html#28 Computer virus strikes US Marshals, FBI affected
https://www.garlic.com/~lynn/2009i.html#22 My Vintage Dream PC
https://www.garlic.com/~lynn/2009l.html#20 Cyber attackers empty business accounts in minutes
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Voltage SecureData Now Provides Distributed End-to-End Encryption of Sensitive Data Date: 14 Sep, 2009 Blog: Payment Systems Networkre:
the x-over comment from the mainframe experts group included reference to this:
Alliance proposes new rules for payments in U.S.
http://www.contactlessnews.com/2009/09/10/alliance-proposes-new-rules-for-payments-in-u-s
but then from earlier today ...
Heartland CEO: Credit card encryption needed
http://www.computerworld.com/s/article/9138008/Heartland_CEO_Credit_card_encryption_needed
Heartland CEO: Credit card encryption needed
http://www.networkworld.com/news/2009/092309-credit-card-standards.html
Heartland CEO: Credit Card Encryption Needed
http://www.pcworld.com/businesscenter/article/171943/heartland_ceo_credit_card_encryption_needed.html
and back to the other side:
Contactless Chip Cards as an Alternative to End-to-End Encryption
http://www.paymentsnews.com/2009/09/smart-card-alliance-suggests-chip-cards-to-deal-with-data-breaches.html
another article from dark reading:
Smart Card Alliance: End-To-End Encryption Won't Stop Credit-Card Fraud
http://www.darkreading.com/database_security/security/encryption/showArticle.jhtml?articleID=220000501
related discussion in information security network:
http://www.linkedin.com/groupAnswers?viewQuestionAndAnswers=
http://www.linkedin.com/groupAnswers?viewQuestionAndAnswers=
http://www.linkedin.com/groupAnswers?viewQuestionAndAnswers=http://www.linkedin.com/groupAnswers?viewQuestionAndAnswers=&gid=80784&discussionID=7148147gid=80784http://www.linkedin.com/groupAnswers?viewQuestionAndAnswers=&gid=80784&discussionID=7148147discussionID=7148147gid=80784http://www.linkedin.com/groupAnswers?viewQuestionAndAnswers=&gid=80784&discussionID=7148147discussionID=7148147gid=80784http://www.linkedin.com/groupAnswers?viewQuestionAndAnswers=&gid=80784&discussionID=7148147discussionID=7148147
some of above, also archived here:
https://www.garlic.com/~lynn/2009n.html#7
which references more detailed article:
http://www.smartcardalliance.org/pages/publications-end-to-end-encryption-and-chip-cards-in-the-us-payments-industry
however, I've frequently mentioned that X9.59 financial standard
(also) tweaked the paradigm so that the information was made useless
to the crooks ... and therefore eliminated the need for end-to-end
encryption. Part of the work in x9a10 financial standard working
group looking at lots of business processes that required access to
information in the transaction. As a result, any *REAL* end-to-end
encryption (from the consumer to the consumer's issuing financial
institution) would require a large amount of decryption &
reencryption, in order to allow normal business processes access to
the information. The X9.59 alternative was to assume that the
information might be accessed possibly thousands of times ... but
eliminate the ability to use the information for fraudulent transactions
https://www.garlic.com/~lynn/x959.html#x959
as an aside ... not only is the smart card alliance discussion similar to what is already defined for x9.59
but also the nacha trials ... rfi response ...
https://www.garlic.com/~lynn/nacharfi.htm
and the results of the NACHA trials (23july2001)
https://web.archive.org/web/20070706004855/http://internetcouncil.nacha.org/News/news.html
as mentioned elsewhere ... in that time frame, there was something of a major deployment failure of a hardware token in consumer market segment ... that tainted all other consumer hardware token activities (in the particular failed deployment, it wasn't actually the hardware token ... but the characteristic of the serial-port card acceptor device that was part of the deployment).
however, out of all this ... there was a standard field definition included as part the international ISO 8583 standard (credit card and debit card networks) for carrying such an authentication value.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: OSS's Simple Sabotage Field Manual Newsgroups: alt.folklore.computers Date: Mon, 14 Sep 2009 23:19:18 -0400recent article in financial cryptography pointed to:
OSS's Simple Sabotage Field Manual
https://svn.cacert.org/CAcert/CAcert_Inc/Board/oss/OSS_Simple_Sabotage_Manual.pdf
with some special focus on
https://svn.cacert.org/CAcert/CAcert_Inc/Board/oss/oss_sabotage.html
as noted ... some of this reads like standard corporate manager's
manual (or maybe dilbert)
(1) Insist on doing everything through "channels." Never permit
short-cuts to be taken in order to, expedite decisions.
(2) Make "speeches." Talk as frequently as possible and at great
length. Illustrate your "points" by long anecdotes and accounts of
personal experiences. Never hesitate to make a few appropriate
"patriotic" comments.
(3) When possible, refer all matters to committees, for "further study
and consideration." Attempt to make the committees as large as possible
- never less than five.
(4) Bring up irrelevant issues as frequently as possible.
(5) Haggle over precise wordings of communications, minutes,
resolutions.
(6) Refer back to matters decided upon at the last meeting and attempt
to reopen the question of the advisability of that decision.
(7) Advocate "caution." Be "reasonable" and urge your fellow-conferees
to be "reasonable" and avoid haste which might result in embarrassments
or difficulties later on.
(8) Be worried about the propriety of any decision -raise the question
of whether such action as is contemplated lies within the jurisdiction
of the group or whether it might conflict with the policy of some higher
echelon.
... snip ...
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: OSS's Simple Sabotage Field Manual Newsgroups: alt.folklore.computers Date: Tue, 15 Sep 2009 10:15:28 -0400Walter Bushell <proto@panix.com> writes:
CAcert is an organization that issues ssl digital certificates ... but their "root" certificate isn't possibly precluded in your browser. the "error" is actually a message that indicates that the "root" certificate is not one known by your browser (hasn't yet been preloaded into your browser by the browser manufacturer).
this is different error from a situation where a website is claiming to be one URL and is using a certificate for some other URL (incorrect as opposed to unknown).
it is possible to continue and fetch the manual pages ... even if it is an untrusted/unknwon (by your browser) certificate ... should not pose any more threat than doing straight http (as opposed to https).
long ago and far away ... we had been called to consult with small client/server startup that wanted to do payment transactions on their server ... the started had also invented this technology they called SSL they wanted to use. as part of doing this thing that is now commonly called "electronic commerce" ... we had to do some end-to-end walk thru of these new operations called themselves Certification Authorities ...and issueing this things called SSL digital certificates.
somewhat after that we would mention that there were lots of reasons
(weaknesses) to refer to the certificates as "comfort" (as opposed to
security) ... misc. past posts
https://www.garlic.com/~lynn/subpubkey.html#sslcert
especially with lots of hype about how safe, certificates, should make you feel.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Some companies are selling the idea that you can use just a (prox) physical access badge (single factor) for logical access as acceptable Date: 15 Sep, 2009 Blog: Information Security Networksecurity proportional to risk .... multi-factor authentication is nominally assumed to be more secure ... based on implicit assumptions that the different factors have independent threats & vulnerabilities. For instance, (two-factor) pin/password is frequently assumed to be countermeasure to lost/stolen badge.
what is probability of lost/stolen badge being used fraudulently as single factor authentication and what is at risk if it happens.
a growing issue is the large proliferation in shared-secret paradigm as an authentication factor (whether multi-factor PIN in conjunction with some sort of physical token ... or single-factor like a password) ... along with implicit assumptions about unique shared-secret for every security domain ... has resulted in people having to memorize large scores of impossible to remember shared-secrets. this is poor human factors since it isn't feasible or sustainable situation ... resulting in situations where people have to write down/record the values.
some studies have found that 1/3rd of multi-factor something you have physical tokens have pin/password written on them. other situations may have the token being carried in a wallet ... which also contains list of pin/passwords; a wallet frequently represents a common lost/stolen item (both the token and the recorded pin/passwords) ... invalidating any implicit assumption about independent vulnerabilities.
slightly related:
Users Prefer Device Fingerprinting to Passwords
http://www.internetnews.com/ec-news/article.php/3839071/Users+Prefer+Device+Fingerprinting+to+Passwords.htm
from above:
Study finds 70 percent of respondents say they'd be willing to have
their PCs and mobile devices authenticated by an online merchant
before completing a transaction.
... snip ...
Part of the work in the x9a10 financial standard working group on
x9.59 financial standard (in the mid-90s had been given the
requirement to preserve the integrity of the financial infrastructure
for all retail payments) ... some refs
https://www.garlic.com/~lynn/x959.html#x959
was that the same x9.59 standard concurrently support wide variety of one-factor, two-factor and/or even three-factor authentication ... even possibly dynamically changing the factors and/or combination of factors based on transaction value &/or risk (security proportional to risk & parameterised risk management).
correspondingly ... work on the AADS chip strawman (security
proportional to risk & parameterised risk management)... was that
the same chip would work as single-factor authentication as well as
various combinations of two-factor and/or even three-factor
authentication.
https://www.garlic.com/~lynn/x959.html#aads
In the 90s, I had semi-facetiously said I would take a $500 milspec part and aggresively cost-reduce it while improving security ... eventually getting close to EPC RFID chip cost (i.e. the RFID chips being targeted to replace UPC bar-codes on grocery store items) w/o sacrificing security.
The goal, I eventually characterized as removing all the inhibitors to being able to shift from a "institutional centric" paradigm to a person-centric paradigm ... where potentially a person could use the same hardware token for a huge variety of different purposes operating in a wide variety of different ways (i.e. being able to support a person-centric paradigm would embody, at least, security proportional to risk and parameterised risk management).
In enabling person-centric ... the same hardware token would be able to operate as a (single-factor, something you have) for door-entry as well as for higher security physical access ... as well as both low-value and high-value financial transactions ... as well as multitude of other authentication purposes ... operating in a variety of ways.
misc. past posts mentioning 3-factor authentication paradigm
https://www.garlic.com/~lynn/subintegrity.html#3factor
semi-custom chip was a few hundred thousand circuits ... I got it evaluated at EAL4+ ... wanted to go for higher ... but didn't have a crypto profile to evaluate against. first pass at complete custom chip was 40k circuits. Basically chip cost (in volume) is cost of the wafer and number of chips per wafer. In the late 90s, increasingly smaller chips ran into road block because the area for cutting the wafer into individuals chips ... was becoming larger than the total chip area. Next step in getting ever increasing larger number of smaller chips from a wafer was coming up with new wafer cutting technology (to drastically reduce the area lost to the cuts).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Malware lingers months on infected PCs Date: 15 Sep, 2009 Blog: Computer Security and ForensicsMalware lingers months on infected PCs
from above:
Resident evil Malware stays around on infected PCs far longer than
previously thought, according to the latest research from Trend
Micro.... Web threats: Why conventional protection doesn't work
... snip ...
and somewhat related ...
Australian ISPs Asked To Cut Off Malware-Infected PCs
http://it.slashdot.org/story/09/09/15/0429234/Australian-ISPs-Asked-To-Cut-Off-Malware-Infected-PCs
ISPs asked to cut off malware-infected PCs
http://www.itnews.com.au/News/155673,isps-asked-to-cut-off-malware-infected-pcs.aspx
I raised this as an option in 1995. We had been called in to consult with a small client/server startup that wanted to do payment transactions on their server ... and the startup had invented this technology they wanted to use called "SSL" ... the result is now frequently called "electronic commerce". As part of this ... we did some detailed threat and vulnerability studies ... including DOS & DDOS attacks.
We identified ISPs as being able to recognize and cut-off compromised PCs that were spewing spam, involved in DDOS attacks, and/or involved in perpetrating infection/compromise. Push-back was that ISP (at the time) didn't have the capability ... we pointed out that even at the time, ISP could recognize & disable multiple concurrent connects (which wouldn't take that much effort to modify to do some of these other tasks). We conjectured at the time, that the push-back was rather 1) it might only be 99.99% effective and 2) doing something ... but not 100% ... might open them to liability litigation.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Existence of early 360 software ( was Re: Continous Systems Modelling Packa Newsgroups: alt.folklore.computers Date: Wed, 16 Sep 2009 09:20:47 -0400Calum <com.gmail@scottishwildcat.nospam> writes:
i was trying to get copies of all vmshare computer conferencing and make
them available on internal machines ... especially the world-wide sales
& marketing HONE machines. I talked to him about using an apple II at
home ... in lieu of my 3101 glass teletype ... to log into tymshare,
download all new & changed vmshare activity ... and then upload into
internal ibm systems ... for distribution on internal machines. some
past pictures of my online home setup (although missing 2741 pictures
used in the early 70s)
https://www.garlic.com/~lynn/lhwemail.html#oldpicts
misc. old posts mentioning world-wide sales&marketing hone
(one of my hobbies during the 70s and much of the 80s):
https://www.garlic.com/~lynn/subtopic.html#hone
misc. old email referencing terminal emulation
https://www.garlic.com/~lynn/subnetwork.html#emulation
misc. old email mentioning vmshare
https://www.garlic.com/~lynn/lhwemail.html#vmshare
online computer conferencing vmshare archives (back to aug76)
http://vm.marist.edu/~vmshare/
note that while this was all pure "text" ... not really executable code
(modulo any "EXEC" stuff) ... so very low probability of introducing
virus and malware on the internal network ... still had lots of dealings
with legal dept. regarding introducing external comtamination (&/or
copyrighted material) into the internal corporation. just part of
getting blamed for computer conferencing on the internal network in the
lates 70s and early 80s. misc. past posts mentioning internal network
https://www.garlic.com/~lynn/subnetwork.html#internalnet
i also got to go to business dinners (before mac was announced) and argue with some of the mac developers.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: 33 Years In IT/Security/Audit To: <ibm-main@bama.ua.edu> Date: Wed, 16 Sep 2009 09:51:40 -0400UI0037288@TECHMAHINDRA.COM (Umamaheshwar Iyer) writes:
for some security related, wang's computer system receives "B3"
security rating
http://findarticles.com/p/articles/mi_m0EIN/is_1995_Oct_5/ai_17531523/
for slight other drift, recent post mentioning getting blamed for
computer conferencing on the internal network in the late 70s and early
80s (from early 360 software thread in a.f.c)
https://www.garlic.com/~lynn/2009n.html#9
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Banks should share cyber crime information IT PRO Date: 16 Sep, 2009 Blog: Financial Crime Risk, Fraud and SecurityBanks should share cyber crime information IT PRO
from above:
Financial institutions in Holland have shared information about cyber
crime for years, offering an example to the UK and Europe about how it
could and should be done.
... snip ...
One of the big issues at the critical infrastructure protection
regarding ISAC (industry information vulnerability, threats, exploit
sharing) was whether the information would be subject to FOIA
http://www.isaccouncil.org/
and
http://www.fsisac.com/
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: 33 Years In IT/Security/Audit Newsgroups: bit.listserv.ibm-main,alt.folklore.computers Date: Wed, 16 Sep 2009 14:00:08 -0400Steve_Thompson@STERCOMM.COM (Thompson, Steve) writes:
there aren't a lot of stuff that had gotten B3 evaluation
... following claims that wang was the only one ...
http://www.dynamoo.com/orange/summary.htm
in the transition from orange book to common criteria, i had started
doing merged security taxonomy & glossary
https://www.garlic.com/~lynn/index.html#glosnote
and some from common criteria was criticizing me for having both orange book and common criteria definitions in the same glossary. i countered with common criteria was to have protection profiles for specific environments that weren't otherwise capable of getting reasonable orange book certification.
this is recent post referencing getting EAL4+ evaluation for a
semi-custom chip
https://www.garlic.com/~lynn/2009n.html#7
my complaint was that some others, using similar flavor of the chip, being able to get a higher evaluation. they were able to use "smart card protection profile" ... which has majority of the stuff about being able to load applications on the chip (doesn't actually evaluate what gets loaded to make the chip useful ... just evaluates the chip and the loading processes ... not what is loaded).
my semi-custom chip had whole bunch of the applications in silicon ... including crypto. since it was part of the silicon chip ... it had to be evaluated as part of the basic chip (the other way avoided having to evaluate a useful deployed chip with actual application). the problem was that there wasn't profile for the crypto for higher level evaluation. I would still claim that my base EAL4+ chip was actually more secure chip than those with higher evaluations ... since I had done with the applications and they evaluated w/o actual applications.
not long ago there was presentation on 65 system EAL evaluations ... that claimed 63 had undisclosed/unpublished deviations (i.e. they had unpublished changes to the protection profile being used). In theory, the purpose behind all this is to have apple-to-apple (trusted operation) comparison ... but with majority having various undisclosed deviations ... it is hard to see how they aren't apple-to-oranges.
It turns out I was involved in doing some amount of trusted computing
stuff as undergraduate in the 60s ... even if I didn't know it was
called that at the time ... and I didn't learn about these guys until
much later
https://web.archive.org/web/20090117083033/http://www.nsa.gov/research/selinux/list-archive/0409/8362.shtml
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: UK issues Turning apology (and about time, too) Newsgroups: alt.folklore.computers Date: Wed, 16 Sep 2009 15:42:21 -0400Eric Chomko <pne.chomko@comcast.net> writes:
The no-down, no-documentation, 1% introductory rate, interest only payment ARMs ... became enormously attractive to the speculators ... since the carrying cost was much less than real estate inflation rate in many parts of the country (planning on flipping before the rates adjusted) .... speculators would obtain every one they possible could, the loan originators would write every one they possible could ... and then unload them as triple-A rated toxic CDOs.
Repeal of Glass-Steagall (keeping regulated depository institutions separate from unregulated investment banking) ... as part of bank modernization act ... then had some of the large (regulated) consumer banks with (unregulated) investment banking arms ... buying up the toxic CDOs ... at enormous leverage and carrying them off-balance sheet. These (regulated) banks hadn't necessarily had anything to do with the original mortgages ... but were providing (via unregulated investment banking operatings) much of the fuel in around about, circuitous manner (skirting traditional regulation ... where regulated depository institutions had previously been making regulated mortgages using deposits as source of funds).
There was big major failing in SEC providing oversite of the rating agencies ... which was major factor in allowing the whole house of cards to operate (unjustified triple-A rating on toxic CDOs, enormously increasing the source funds for unregulated load originators). The repeal of Glass-Steagall allowed large regulated depository institutions to play a major role in these unregulated mortgages ... with their unregulated investment purchasing major amounts of the triple-A rated toxic (mortgage backed) toxic CDOs.
The speculation frenzy ... created the impression that the housing demand was significantly larger than it actually was. The apparent (speculation) spike in demand motivated builders to big uptick in building. When the whole speculation bubble bursts ... there is both deflation in (speculation bubble) prices as well as having to work off the excessive building/inventory. The bursting speculation bubble results in all sorts of other kinds of collateral damage thruout the economy.
Past couple days, there has been a number of articles and news
commentary about it being one year since the bubble burst (marked by
lehman demise) ... and that financial lobby has spent over $3b on
lobbying to prevent any congress from making changes in the basic
environment that resulted in the whole mess (some comment at least six
financial lobbiests thundering up and down the halls of congress for
every congressman). There was snide comment on CPAN this past weekend
... that the $3B is cheap price for the $27T that the financial industry
was able to suck out of the infrastructure creating the current
financial mess.
Evil Wall Street Exports Boomed With 'Fools' Born to Buy Debt
https://www.bloomberg.com/news/articles/2008-10-27/evil-wall-street-exports-boomed-with-fools-born-to-buy-debt
a couple of the anniversary articles:
Rogues' Gallery Revisited
http://www.forbes.com/2009/09/08/fuld-cayne-thain-lehman-paulson-pandit-opinions-contributors-charles-gasparino.html
Where are the subprime perp walks?
http://money.cnn.com/2009/09/15/news/subprime.perpwalk.fortune/index.htm?postversion=2009091517
misc. past posts mentioning rating agencies & triple-A ratings on toxic
CDOs, Lehman having marginal chance of surviving playing long/short
mismatch (even if they hadn't been dealing in toxic CDOs), repeal
of glass-steagall, etc:
https://www.garlic.com/~lynn/2008.html#66 As Expected, Ford Falls From 2nd Place in U.S. Sales
https://www.garlic.com/~lynn/2008b.html#12 Computer Science Education: Where Are the Software Engineers of Tomorrow?
https://www.garlic.com/~lynn/2008b.html#75 Toyota Sales for 2007 May Surpass GM
https://www.garlic.com/~lynn/2008c.html#11 Toyota Sales for 2007 May Surpass GM
https://www.garlic.com/~lynn/2008c.html#87 Toyota Sales for 2007 May Surpass GM
https://www.garlic.com/~lynn/2008d.html#85 Toyota Sales for 2007 May Surpass GM
https://www.garlic.com/~lynn/2008e.html#42 Banks failing to manage IT risk - study
https://www.garlic.com/~lynn/2008e.html#59 independent appraisers
https://www.garlic.com/~lynn/2008e.html#70 independent appraisers
https://www.garlic.com/~lynn/2008f.html#1 independent appraisers
https://www.garlic.com/~lynn/2008f.html#13 independent appraisers
https://www.garlic.com/~lynn/2008f.html#17 independent appraisers
https://www.garlic.com/~lynn/2008f.html#43 independent appraisers
https://www.garlic.com/~lynn/2008f.html#46 independent appraisers
https://www.garlic.com/~lynn/2008f.html#51 independent appraisers
https://www.garlic.com/~lynn/2008f.html#53 independent appraisers
https://www.garlic.com/~lynn/2008f.html#71 Bush - place in history
https://www.garlic.com/~lynn/2008f.html#73 Bush - place in history
https://www.garlic.com/~lynn/2008f.html#75 Bush - place in history
https://www.garlic.com/~lynn/2008f.html#77 Bush - place in history
https://www.garlic.com/~lynn/2008f.html#79 Bush - place in history
https://www.garlic.com/~lynn/2008f.html#94 Bush - place in history
https://www.garlic.com/~lynn/2008f.html#96 Bush - place in history
https://www.garlic.com/~lynn/2008f.html#97 Bush - place in history
https://www.garlic.com/~lynn/2008g.html#2 Bush - place in history
https://www.garlic.com/~lynn/2008g.html#4 CDOs subverting Boyd's OODA-loop
https://www.garlic.com/~lynn/2008g.html#16 independent appraisers
https://www.garlic.com/~lynn/2008g.html#32 independent appraisers
https://www.garlic.com/~lynn/2008g.html#44 Fixing finance
https://www.garlic.com/~lynn/2008g.html#51 IBM CEO's remuneration last year ?
https://www.garlic.com/~lynn/2008g.html#52 IBM CEO's remuneration last year ?
https://www.garlic.com/~lynn/2008g.html#57 Credit crisis could cost nearly $1 trillion, IMF predicts
https://www.garlic.com/~lynn/2008g.html#59 Credit crisis could cost nearly $1 trillion, IMF predicts
https://www.garlic.com/~lynn/2008g.html#62 Credit crisis could cost nearly $1 trillion, IMF predicts
https://www.garlic.com/~lynn/2008g.html#64 independent appraisers
https://www.garlic.com/~lynn/2008g.html#66 independent appraisers
https://www.garlic.com/~lynn/2008g.html#67 independent appraisers
https://www.garlic.com/~lynn/2008h.html#1 subprime write-down sweepstakes
https://www.garlic.com/~lynn/2008h.html#28 subprime write-down sweepstakes
https://www.garlic.com/~lynn/2008h.html#32 subprime write-down sweepstakes
https://www.garlic.com/~lynn/2008h.html#48 subprime write-down sweepstakes
https://www.garlic.com/~lynn/2008h.html#49 subprime write-down sweepstakes
https://www.garlic.com/~lynn/2008h.html#89 Credit Crisis Timeline
https://www.garlic.com/~lynn/2008h.html#90 subprime write-down sweepstakes
https://www.garlic.com/~lynn/2008i.html#4 A Merit based system of reward -Does anybody (or any executive) really want to be judged on merit?
https://www.garlic.com/~lynn/2008i.html#30 subprime write-down sweepstakes
https://www.garlic.com/~lynn/2008i.html#64 Is the credit crunch a short term aberation
https://www.garlic.com/~lynn/2008i.html#77 Do you think the change in bankrupcy laws has exacerbated the problems in the housing market leading more people into forclosure?
https://www.garlic.com/~lynn/2008i.html#104 dollar coins
https://www.garlic.com/~lynn/2008j.html#3 dollar coins
https://www.garlic.com/~lynn/2008j.html#9 dollar coins
https://www.garlic.com/~lynn/2008j.html#12 To: Graymouse -- Ireland and the EU, What in the H... is all this about?
https://www.garlic.com/~lynn/2008j.html#18 dollar coins
https://www.garlic.com/~lynn/2008j.html#22 dollar coins
https://www.garlic.com/~lynn/2008j.html#23 dollar coins
https://www.garlic.com/~lynn/2008j.html#38 dollar coins
https://www.garlic.com/~lynn/2008j.html#40 dollar coins
https://www.garlic.com/~lynn/2008j.html#46 dollar coins
https://www.garlic.com/~lynn/2008j.html#48 dollar coins
https://www.garlic.com/~lynn/2008j.html#64 lack of information accuracy
https://www.garlic.com/~lynn/2008j.html#66 lack of information accuracy
https://www.garlic.com/~lynn/2008j.html#68 lack of information accuracy
https://www.garlic.com/~lynn/2008j.html#69 lack of information accuracy
https://www.garlic.com/~lynn/2008j.html#71 lack of information accuracy
https://www.garlic.com/~lynn/2008k.html#6 dollar coins
https://www.garlic.com/~lynn/2008k.html#10 Why do Banks lend poorly in the sub-prime market? Because they are not in Banking!
https://www.garlic.com/~lynn/2008k.html#11 dollar coins
https://www.garlic.com/~lynn/2008k.html#12 dollar coins
https://www.garlic.com/~lynn/2008k.html#13 dollar coins
https://www.garlic.com/~lynn/2008k.html#14 dollar coins
https://www.garlic.com/~lynn/2008k.html#16 dollar coins
https://www.garlic.com/~lynn/2008k.html#19 dollar coins
https://www.garlic.com/~lynn/2008k.html#20 IBM's 2Q2008 Earnings
https://www.garlic.com/~lynn/2008k.html#23 dollar coins
https://www.garlic.com/~lynn/2008k.html#27 dollar coins
https://www.garlic.com/~lynn/2008k.html#28 dollar coins
https://www.garlic.com/~lynn/2008k.html#33 dollar coins
https://www.garlic.com/~lynn/2008k.html#36 dollar coins
https://www.garlic.com/~lynn/2008k.html#41 dollar coins
https://www.garlic.com/~lynn/2008l.html#42 dollar coins
https://www.garlic.com/~lynn/2008l.html#44 dollar coins
https://www.garlic.com/~lynn/2008l.html#67 dollar coins
https://www.garlic.com/~lynn/2008l.html#70 dollar coins
https://www.garlic.com/~lynn/2008m.html#12 Fraud due to stupid failure to test for negative
https://www.garlic.com/~lynn/2008m.html#15 Fraud due to stupid failure to test for negative
https://www.garlic.com/~lynn/2008m.html#16 Fraud due to stupid failure to test for negative
https://www.garlic.com/~lynn/2008m.html#26 Fraud due to stupid failure to test for negative
https://www.garlic.com/~lynn/2008m.html#73 Blinkylights
https://www.garlic.com/~lynn/2008m.html#76 When risks go south: FM&FM to be nationalized
https://www.garlic.com/~lynn/2008m.html#80 Fraud due to stupid failure to test for negative
https://www.garlic.com/~lynn/2008m.html#91 Blinkylights
https://www.garlic.com/~lynn/2008m.html#92 Blinkylights
https://www.garlic.com/~lynn/2008m.html#95 Blinkylights
https://www.garlic.com/~lynn/2008m.html#96 Blinkylights
https://www.garlic.com/~lynn/2008m.html#99 Blinkylights
https://www.garlic.com/~lynn/2008n.html#3 Blinkylights
https://www.garlic.com/~lynn/2008n.html#12 Blinkylights
https://www.garlic.com/~lynn/2008n.html#14 Blinkylights
https://www.garlic.com/~lynn/2008n.html#19 Blinkylights
https://www.garlic.com/~lynn/2008n.html#21 Michigan industry
https://www.garlic.com/~lynn/2008n.html#23 Michigan industry
https://www.garlic.com/~lynn/2008n.html#24 Blinkylights
https://www.garlic.com/~lynn/2008n.html#25 Blinkylights
https://www.garlic.com/~lynn/2008n.html#33 Blinkylights
https://www.garlic.com/~lynn/2008n.html#37 Success has many fathers, but failure has the US taxpayer
https://www.garlic.com/~lynn/2008n.html#40 Success has many fathers, but failure has the US taxpayer
https://www.garlic.com/~lynn/2008n.html#42 Blinkylights
https://www.garlic.com/~lynn/2008n.html#44 VMware Chief Says the OS Is History
https://www.garlic.com/~lynn/2008n.html#49 VMware Chief Says the OS Is History
https://www.garlic.com/~lynn/2008n.html#53 Your thoughts on the following comprehensive bailout plan please
https://www.garlic.com/~lynn/2008n.html#74 Why can't we analyze the risks involved in mortgage-backed securities?
https://www.garlic.com/~lynn/2008n.html#78 Isn't it the Federal Reserve role to oversee the banking system??
https://www.garlic.com/~lynn/2008n.html#88 Blinkylights
https://www.garlic.com/~lynn/2008n.html#94 Blinkylights
https://www.garlic.com/~lynn/2008n.html#95 Blinkylights
https://www.garlic.com/~lynn/2008n.html#99 Blinkylights
https://www.garlic.com/~lynn/2008o.html#12 The human plague
https://www.garlic.com/~lynn/2008o.html#15 Financial Crisis - the result of uncontrolled Innovation?
https://www.garlic.com/~lynn/2008o.html#18 Once the dust settles, do you think Milton Friedman's economic theories will be laid to rest
https://www.garlic.com/~lynn/2008o.html#19 What's your view of current global financial / economical situation?
https://www.garlic.com/~lynn/2008o.html#26 SOX (Sarbanes-Oxley Act), is this really followed and worthful considering current Financial Crisis?
https://www.garlic.com/~lynn/2008o.html#28 Does anyone get the idea that those responsible for containing this finanical crisis are doing too much?
https://www.garlic.com/~lynn/2008o.html#31 The human plague
https://www.garlic.com/~lynn/2008o.html#37 The human plague
https://www.garlic.com/~lynn/2008o.html#39 The human plague
https://www.garlic.com/~lynn/2008o.html#42 The human plague
https://www.garlic.com/~lynn/2008o.html#43 The human plague
https://www.garlic.com/~lynn/2008o.html#44 The human plague
https://www.garlic.com/~lynn/2008o.html#45 The human plague
https://www.garlic.com/~lynn/2008o.html#51 Why are some banks failing, and others aren't?
https://www.garlic.com/~lynn/2008o.html#52 Why is sub-prime crisis of America called the sub-prime crisis?
https://www.garlic.com/~lynn/2008o.html#62 Would anyone like to draw a diagram of effects or similar for the current "credit crisis"?
https://www.garlic.com/~lynn/2008o.html#65 Can the financial meltdown be used to motivate sustainable development in order to achieve sustainable growth and desired sustainability?
https://www.garlic.com/~lynn/2008o.html#68 Blinkenlights
https://www.garlic.com/~lynn/2008o.html#71 Why is sub-prime crisis of America called the sub-prime crisis?
https://www.garlic.com/~lynn/2008o.html#74 Would anyone like to draw a diagram of effects or similar for the current "credit crisis"?
https://www.garlic.com/~lynn/2008o.html#75 In light of the recent financial crisis, did Sarbanes-Oxley fail to work?
https://www.garlic.com/~lynn/2008o.html#78 Who murdered the financial system?
https://www.garlic.com/~lynn/2008o.html#80 Can we blame one person for the financial meltdown?
https://www.garlic.com/~lynn/2008o.html#82 Greenspan testimony and securization
https://www.garlic.com/~lynn/2008o.html#83 Chip-and-pin card reader supply-chain subversion 'has netted millions from British shoppers'
https://www.garlic.com/~lynn/2008p.html#3 Blinkenlights
https://www.garlic.com/~lynn/2008p.html#8 Global Melt Down
https://www.garlic.com/~lynn/2008p.html#9 Do you believe a global financial regulation is possible?
https://www.garlic.com/~lynn/2008p.html#47 In Modeling Risk, the Human Factor Was Left Out
https://www.garlic.com/~lynn/2008p.html#60 Did sub-prime cause the financial mess we are in?
https://www.garlic.com/~lynn/2008p.html#70 Is there any technology that we are severely lacking in the Financial industry?
https://www.garlic.com/~lynn/2008p.html#77 Tell me why the taxpayer should be saving GM and Chrysler (and Ford) managers & shareholders at this stage of the game?
https://www.garlic.com/~lynn/2008q.html#10 realtors (and GM, too!)
https://www.garlic.com/~lynn/2008q.html#11 Blinkenlights
https://www.garlic.com/~lynn/2008q.html#12 Blinkenlights
https://www.garlic.com/~lynn/2008q.html#19 Collateralized debt obligations (CDOs)
https://www.garlic.com/~lynn/2008q.html#20 How is Subprime crisis impacting other Industries?
https://www.garlic.com/~lynn/2008q.html#26 Blinkenlights
https://www.garlic.com/~lynn/2008q.html#28 Blinkenlights
https://www.garlic.com/~lynn/2008q.html#32 I was wondering what types of frauds the audience think will increase?
https://www.garlic.com/~lynn/2008q.html#49 Have not the following principles been practically disproven, once and for all, by the current global financial meltdown?
https://www.garlic.com/~lynn/2008q.html#50 Obama, ACORN, subprimes (Re: Spiders)
https://www.garlic.com/~lynn/2008q.html#57 Blinkenlights
https://www.garlic.com/~lynn/2008q.html#58 Obama, ACORN, subprimes (Re: Spiders)
https://www.garlic.com/~lynn/2008q.html#66 Blinkenlights
https://www.garlic.com/~lynn/2008q.html#68 Obama, ACORN, subprimes (Re: Spiders)
https://www.garlic.com/~lynn/2008q.html#69 if you are an powerful financial regulator , how would you have stopped the credit crunch?
https://www.garlic.com/~lynn/2008r.html#4 Basel Committee outlines plans to strengthen Basel II
https://www.garlic.com/~lynn/2008r.html#10 Blinkylights
https://www.garlic.com/~lynn/2008r.html#35 Blinkenlights
https://www.garlic.com/~lynn/2008r.html#58 Blinkenlights
https://www.garlic.com/~lynn/2008r.html#64 Is This a Different Kind of Financial Crisis?
https://www.garlic.com/~lynn/2008r.html#67 What is securitization and why are people wary of it ?
https://www.garlic.com/~lynn/2008s.html#8 Top financial firms of US are eyeing on bailout. It implies to me that their "Risk Management Department's" assessment was way below expectations
https://www.garlic.com/~lynn/2008s.html#9 Blind-sided, again. Why?
https://www.garlic.com/~lynn/2008s.html#20 Five great technological revolutions
https://www.garlic.com/~lynn/2008s.html#23 Garbage in, garbage out trampled by Moore's law
https://www.garlic.com/~lynn/2008s.html#24 Garbage in, garbage out trampled by Moore's law
https://www.garlic.com/~lynn/2008s.html#30 How reliable are the credit rating companies? Who is over seeing them?
https://www.garlic.com/~lynn/2008s.html#35 Is American capitalism and greed to blame for our financial troubles in the US?
https://www.garlic.com/~lynn/2008s.html#55 Is this the story behind the crunchy credit stuff?
https://www.garlic.com/~lynn/2008s.html#59 Garbage in, garbage out trampled by Moore's law
https://www.garlic.com/~lynn/2008s.html#70 Garbage in, garbage out trampled by Moore's law
https://www.garlic.com/~lynn/2009.html#14 What are the challenges in risk analytics post financial crisis?
https://www.garlic.com/~lynn/2009.html#15 What are the challenges in risk analytics post financial crisis?
https://www.garlic.com/~lynn/2009.html#21 Banks to embrace virtualisation in 2009: survey
https://www.garlic.com/~lynn/2009.html#31 Banks to embrace virtualisation in 2009: survey
https://www.garlic.com/~lynn/2009.html#32 What are the challenges in risk analytics post financial crisis?
https://www.garlic.com/~lynn/2009.html#42 Lets play Blame Game...?
https://www.garlic.com/~lynn/2009.html#52 The Credit Crunch: Why it happened?
https://www.garlic.com/~lynn/2009.html#58 HONEY I LOVE YOU, but please cut the cards
https://www.garlic.com/~lynn/2009.html#63 CROOKS and NANNIES: what would Boyd do?
https://www.garlic.com/~lynn/2009.html#73 CROOKS and NANNIES: what would Boyd do?
https://www.garlic.com/~lynn/2009.html#74 CROOKS and NANNIES: what would Boyd do?
https://www.garlic.com/~lynn/2009.html#77 CROOKS and NANNIES: what would Boyd do?
https://www.garlic.com/~lynn/2009.html#79 The Credit Crunch: Why it happened?
https://www.garlic.com/~lynn/2009.html#80 Are reckless risks a natural fallout of "excessive" executive compensation ?
https://www.garlic.com/~lynn/2009.html#84 what was the idea behind Citigroup's splitting up into two different divisions? what does this do for citigroup?
https://www.garlic.com/~lynn/2009b.html#1 Are Both The U.S. & UK on the brink of debt disaster?
https://www.garlic.com/~lynn/2009b.html#23 BarCampBank - informal finance rantathon in London
https://www.garlic.com/~lynn/2009b.html#25 The recently revealed excesses of John Thain, the former CEO of Merrill Lynch, while the firm was receiving $25 Billion in TARP funds makes me sick
https://www.garlic.com/~lynn/2009b.html#37 A great article was posted in another BI group: "To H*** with Business Intelligence: 40 Percent of Execs Trust Gut"
https://www.garlic.com/~lynn/2009b.html#48 The blame game is on : A blow to the Audit/Accounting Industry or a lesson learned ???
https://www.garlic.com/~lynn/2009b.html#49 US disaster, debts and bad financial management
https://www.garlic.com/~lynn/2009b.html#51 Will the Draft Bill floated in Congress yesterday to restrict trading of naked Credit Default Swaps help or aggravate?
https://www.garlic.com/~lynn/2009b.html#52 What has the Global Financial Crisis taught the Nations, it's Governments and Decision Makers, and how should they apply that knowledge to manage risks differently in the future?
https://www.garlic.com/~lynn/2009b.html#53 Credit & Risk Management ... go Simple ?
https://www.garlic.com/~lynn/2009b.html#54 In your opinion, which facts caused the global crise situation?
https://www.garlic.com/~lynn/2009b.html#57 Credit & Risk Management ... go Simple ?
https://www.garlic.com/~lynn/2009b.html#58 OCR scans of old documents
https://www.garlic.com/~lynn/2009b.html#59 As bonuses...why breed greed, when others are in dire need?
https://www.garlic.com/~lynn/2009b.html#60 OCR scans of old documents
https://www.garlic.com/~lynn/2009b.html#73 What can we learn from the meltdown?
https://www.garlic.com/~lynn/2009b.html#78 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009b.html#79 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009b.html#80 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#0 Audit II: Two more scary words: Sarbanes-Oxley
https://www.garlic.com/~lynn/2009c.html#1 Audit II: Two more scary words: Sarbanes-Oxley
https://www.garlic.com/~lynn/2009c.html#6 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#8 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#10 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#11 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#16 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#18 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#20 Decision Making or Instinctive Steering?
https://www.garlic.com/~lynn/2009c.html#29 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#32 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#36 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#38 People to Blame for the Financial Crisis
https://www.garlic.com/~lynn/2009c.html#39 'WHO IS RESPONSIBLE FOR THE GLOBAL MELTDOWN'
https://www.garlic.com/~lynn/2009c.html#42 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#46 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#51 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#53 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#55 Who will give Citigroup the KNOCKOUT blow?
https://www.garlic.com/~lynn/2009c.html#61 Accounting for the "greed factor"
https://www.garlic.com/~lynn/2009c.html#65 is it possible that ALL banks will be nationalized?
https://www.garlic.com/~lynn/2009c.html#67 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009d.html#0 PNC Financial to pay CEO $3 million stock bonus
https://www.garlic.com/~lynn/2009d.html#7 Are Ctibank's services and products so vital to global economy than no other banks can substitute it?
https://www.garlic.com/~lynn/2009d.html#10 Who will Survive AIG or Derivative Counterparty Risk?
https://www.garlic.com/~lynn/2009d.html#16 The Formula That Killed Wall Street
https://www.garlic.com/~lynn/2009d.html#18 HSBC is expected to announce a profit, which is good, what did they do differently?
https://www.garlic.com/~lynn/2009d.html#22 Is it time to put banking executives on trial?
https://www.garlic.com/~lynn/2009d.html#28 I need insight on the Stock Market
https://www.garlic.com/~lynn/2009d.html#37 NEW SEC (Enforcement) MANUAL, A welcome addition
https://www.garlic.com/~lynn/2009d.html#42 Bernard Madoff Is Jailed After Pleading Guilty -- are there more "Madoff's" out there?
https://www.garlic.com/~lynn/2009d.html#46 Bernanke Says Regulators Must Protect Against Systemic Risks
https://www.garlic.com/~lynn/2009d.html#61 Quiz: Evaluate your level of Spreadsheet risk
https://www.garlic.com/~lynn/2009d.html#62 Is Wall Street World's Largest Ponzi Scheme where Madoff is Just a Poster Child?
https://www.garlic.com/~lynn/2009d.html#63 Do bonuses foster unethical conduct?
https://www.garlic.com/~lynn/2009d.html#73 Should Glass-Steagall be reinstated?
https://www.garlic.com/~lynn/2009d.html#74 Why is everyone talking about AIG bonuses of millions and keeping their mouth shut on billions sent to foreign banks?
https://www.garlic.com/~lynn/2009d.html#77 Who first mentioned Credit Crunch?
https://www.garlic.com/~lynn/2009e.html#0 What is swap in the financial market?
https://www.garlic.com/~lynn/2009e.html#8 The background reasons of Credit Crunch
https://www.garlic.com/~lynn/2009e.html#13 Should we fear and hate derivatives?
https://www.garlic.com/~lynn/2009e.html#15 The background reasons of Credit Crunch
https://www.garlic.com/~lynn/2009e.html#23 Should FDIC or the Federal Reserve Bank have the authority to shut down and take over non-bank financial institutions like AIG?
https://www.garlic.com/~lynn/2009e.html#30 Timeline: 40 years of OS milestones
https://www.garlic.com/~lynn/2009e.html#35 Architectural Diversity
https://www.garlic.com/~lynn/2009e.html#36 Architectural Diversity
https://www.garlic.com/~lynn/2009e.html#37 How do you see ethics playing a role in your organizations current or past?
https://www.garlic.com/~lynn/2009e.html#40 Architectural Diversity
https://www.garlic.com/~lynn/2009e.html#53 Are the "brightest minds in finance" finally onto something?
https://www.garlic.com/~lynn/2009e.html#59 Tesco to open 30 "bank branches" this year
https://www.garlic.com/~lynn/2009e.html#70 When did "client server" become part of the language?
https://www.garlic.com/~lynn/2009e.html#79 Are the "brightest minds in finance" finally onto something?
https://www.garlic.com/~lynn/2009f.html#2 CEO pay sinks - Wall Street Journal/Hay Group survey results just released
https://www.garlic.com/~lynn/2009f.html#27 US banking Changes- TARP Proposl
https://www.garlic.com/~lynn/2009f.html#29 What is the real basis for business mess we are facing today?
https://www.garlic.com/~lynn/2009f.html#31 What is the real basis for business mess we are facing today?
https://www.garlic.com/~lynn/2009f.html#35 US banking Changes- TARP Proposl
https://www.garlic.com/~lynn/2009f.html#38 On whom or what would you place the blame for the sub-prime crisis?
https://www.garlic.com/~lynn/2009f.html#41 On whom or what would you place the blame for the sub-prime crisis?
https://www.garlic.com/~lynn/2009f.html#43 On whom or what would you place the blame for the sub-prime crisis?
https://www.garlic.com/~lynn/2009f.html#46 Who moved my payment?
https://www.garlic.com/~lynn/2009f.html#47 TARP Disbursements Through April 10th
https://www.garlic.com/~lynn/2009f.html#49 Is the current downturn cyclic or systemic?
https://www.garlic.com/~lynn/2009f.html#51 On whom or what would you place the blame for the sub-prime crisis?
https://www.garlic.com/~lynn/2009f.html#53 What every taxpayer should know about what caused the current Financial Crisis
https://www.garlic.com/~lynn/2009f.html#56 What's your personal confidence level concerning financial market recovery?
https://www.garlic.com/~lynn/2009f.html#65 Just posted third article about toxic assets in a series on the current financial crisis
https://www.garlic.com/~lynn/2009g.html#1 Future of Financial Mathematics?
https://www.garlic.com/~lynn/2009g.html#3 Do the current Banking Results in the US hide a grim truth?
https://www.garlic.com/~lynn/2009g.html#5 Do the current Banking Results in the US hide a grim truth?
https://www.garlic.com/~lynn/2009g.html#7 Just posted third article about toxic assets in a series on the current financial crisis
https://www.garlic.com/~lynn/2009g.html#27 Flawed Credit Ratings Reap Profits as Regulators Fail Investors
https://www.garlic.com/~lynn/2009g.html#31 OODA-loop obfuscation
https://www.garlic.com/~lynn/2009g.html#33 Treating the Web As an Archive
https://www.garlic.com/~lynn/2009g.html#34 Board Visibility Into The Business
https://www.garlic.com/~lynn/2009g.html#37 Future of Financial Mathematics?
https://www.garlic.com/~lynn/2009g.html#52 Future of Financial Mathematics?
https://www.garlic.com/~lynn/2009g.html#53 We Can't Subsidize the Banks Forever
https://www.garlic.com/~lynn/2009g.html#61 Prosecute Bank Execs
https://www.garlic.com/~lynn/2009g.html#76 Undoing 2000 Commodity Futures Modernization Act
https://www.garlic.com/~lynn/2009h.html#3 Consumer Credit Crunch and Banking Writeoffs
https://www.garlic.com/~lynn/2009h.html#10 China's yuan 'set to usurp US dollar' as world's reserve currency
https://www.garlic.com/~lynn/2009h.html#17 REGULATOR ROLE IN THE LIGHT OF RECENT FINANCIAL SCANDALS
https://www.garlic.com/~lynn/2009h.html#22 China's yuan 'set to usurp US dollar' as world's reserve currency
https://www.garlic.com/~lynn/2009h.html#25 The Paradox of Economic Recovery
https://www.garlic.com/~lynn/2009h.html#29 Analysing risk, especially credit risk in Banks, which was a major reason for the current crisis
https://www.garlic.com/~lynn/2009h.html#40 Analysing risk, especially credit risk in Banks, which was a major reason for the current crisis
https://www.garlic.com/~lynn/2009i.html#1 IBM to Build Europe, Asia 'Smart Infrastructure'
https://www.garlic.com/~lynn/2009i.html#13 64 Cores -- IBM is showing a prototype already
https://www.garlic.com/~lynn/2009i.html#23 Why are z/OS people reluctant to use z/OS UNIX? (Are settlements a good argument for overnight batch COBOL ?)
https://www.garlic.com/~lynn/2009i.html#40 64 Cores -- IBM is showing a prototype already
https://www.garlic.com/~lynn/2009i.html#44 64 Cores -- IBM is showing a prototype already
https://www.garlic.com/~lynn/2009i.html#49 What's your personal confidence level concerning financial market recovery?
https://www.garlic.com/~lynn/2009i.html#54 64 Cores -- IBM is showing a prototype already
https://www.garlic.com/~lynn/2009i.html#57 In the USA "financial regulator seeks power to curb excess speculation."
https://www.garlic.com/~lynn/2009i.html#60 In the USA "financial regulator seeks power to curb excess speculation."
https://www.garlic.com/~lynn/2009i.html#74 Administration calls for financial system overhaul
https://www.garlic.com/~lynn/2009i.html#77 Financial Regulatory Reform - elimination of loophole allowing special purpose institutions outside Bank Holding Company (BHC) oversigh
https://www.garlic.com/~lynn/2009j.html#1 Is it possible to have an alternative payment system without riding on the Card Network platforms?
https://www.garlic.com/~lynn/2009j.html#12 IBM identity manager goes big on role control
https://www.garlic.com/~lynn/2009j.html#21 The Big Takeover
https://www.garlic.com/~lynn/2009j.html#35 what is mortgage-backed securities?
https://www.garlic.com/~lynn/2009j.html#36 Average Comp This Year At Top Firm Estimated At $700,000
https://www.garlic.com/~lynn/2009j.html#69 64 Cores -- IBM is showing a prototype already
https://www.garlic.com/~lynn/2009k.html#2 Big Bonuses At Goldman Should Be Applauded, Not Criticized
https://www.garlic.com/~lynn/2009l.html#5 Internal fraud isn't new, but it's news
https://www.garlic.com/~lynn/2009m.html#89 Audits V: Why did this happen to us ;-(
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: UK issues Turning apology (and about time, too) Newsgroups: alt.folklore.computers Date: Wed, 16 Sep 2009 21:01:22 -0400Anne & Lynn Wheeler <lynn@garlic.com> writes:
a few more ..
Financial reforms stalled as Congress returns
http://www.reuters.com/article/ousivMolt/idUSTRE5872CZ20090908
Financial reforms stalled as U.S. Congress returns
http://in.biz.yahoo.com/090908/137/bau5mx.html
Missing Lehman Lesson of Shakeout Means Too Big Banks May Fail
http://www.bloomberg.com/apps/news?pid=20601213
http://www.bloomberg.com/apps/news?pid=20601170&sid=aX8D5utKFuGA
Sleep-At-Night-Money Lost in Lehman Lesson Missing $63 Billion
http://www.bloomberg.com/apps/news?pid=20601170
http://www.bloomberg.com/apps/news?pid=20601170&sid=aLhi.S5xkemY
Lehman Monday Morning Lesson Lost With Obama Regulator-in-Chief
http://www.bloomberg.com/apps/news?pid=20601170
http://www.bloomberg.com/apps/news?pid=20601170&sid=aUTh4YMmI6QE
from above:
He was in a corner office overlooking the White House at the Treasury
Department the next morning, telling Geithner that behemoths such as
Citigroup Inc. and Bank of America Corp. were a menace, he said.
... snip ...
a little search engine use ... from year ago ...
Obama blames lobbyists, politicians for financial crisis
http://www.cnn.com/2008/POLITICS/09/22/campaign.wrap/index.html
Lobbyists for Financial Institutions Swarming All Over the Bailout Bill
http://www.nytimes.com/2008/09/27/business/27lobbyists.html?fta=y
Much blame for financial crisis aimed at Congresses past and present
http://articles.latimes.com/2008/oct/06/business/fi-blame6
Financial Crisis: A Mirror Image of MLM
http://www.falseprofits.com/files/44cfa9c9ee6944ee640541ebc34dbe2a-7.html
from last spring ...
STUDY SHOWS WALL ST. LOBBYISTS SHAPED DEREGULATION BEHIND CRISIS
http://www.albionmonitor.com/0902a/copyright/wallstderegulation.html
Financial sector spent $5 billion lobbying DC last decade: Report
http://www.marketwatch.com/story/financial-sector-spent-5-bln-lobbying-dc
Top Senate Democrat: bankers "own" the U.S. Congress
http://www.salon.com/opinion/greenwald/2009/04/30/ownership/
Sen. Durbin: Bankers 'Own' Congress
http://www.dollarsandsense.org/blog/2009/04/sen-durbin-bankers-own-congress.html
$5 Billion in Lobbying for 12 Corrupt Deals Caused the Multi-Trillion
Dollar Financial Meltdown
http://www.alternet.org/workplace/130683/5_billion_in_lobbying_for_12_corrupt_deals_caused_the_multi-trillion_dollar_financial_meltdown/
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Mainframe Hall of Fame: Three New Members Added Newsgroups: bit.listserv.ibm-main Date: Wed, 16 Sep 2009 22:17:00 -0400BShannon@ROCKETSOFTWARE.COM (Bob Shannon) writes:
STL (since renamed SVL) had started moving vm/4341 systems into conferencing rooms and supply rooms on every floor of the different "towers" ... effectively form of departmental computing (giving rise to the ever increasing number of STLVM* networking nodes on the internal network).
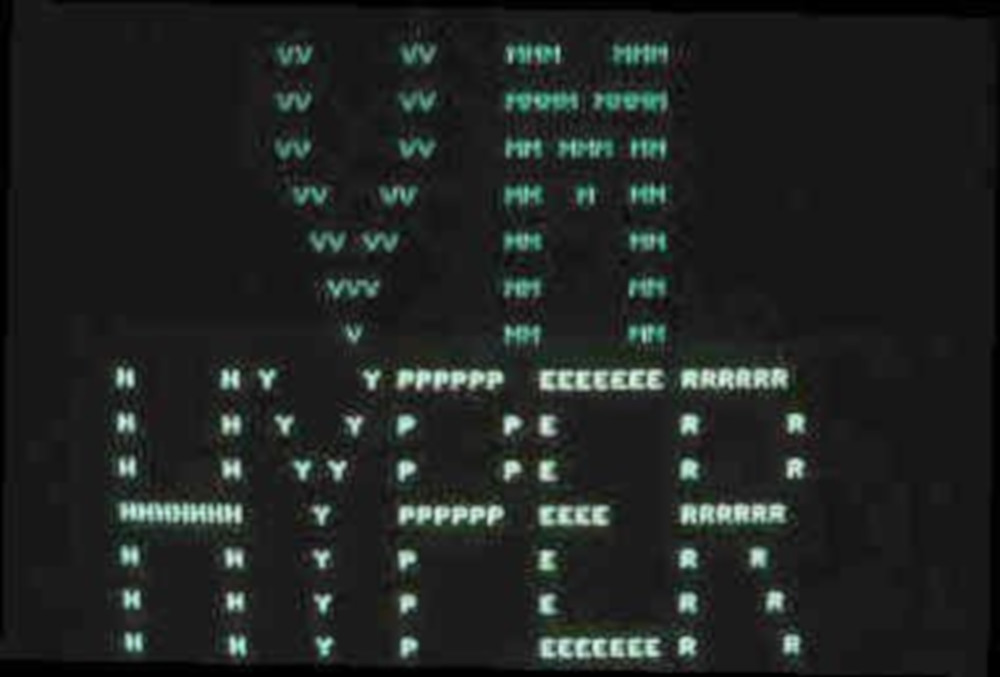
screenshot of vm logo screen ... part of special project I did
for stl datacenter & ims development group
https://www.garlic.com/~lynn/vmhyper.jpg

some STL/SVL views:
http://www.ajnordley.com/IBM/Air/SVL/
the above article mentions the interior couryard between the towers and above "one of the largest computer machine rooms west of the Mississippi". it also mentions flooding of roads ... but when STL first open, the computer room was also getting flooded.
On the other hand ... I had done a stint working at BCS ... and I thot the renton datacenter was much larger.
trivia question: what was going to be the original name for STL??? ... it was changed at the last minute, a week before it was due to open
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Mainframe Hall of Fame: Three New Members Added To: <ibm-main@bama.ua.edu> Date: Thu, 17 Sep 2009 07:38:28 -0400crashlurks@GMAIL.COM (Chris Craddock) writes:
closet post office; (also) the range of hills behind the lab ... look at
the images on the reference ... demarks south san jose and "coyote
valley".
http://www.ajnordley.com/IBM/Air/SVL/
some coyote valley associiation had lobbied the state that the original 101 new/expansion would only be four lanes thru "coyote valley" ... so it changed from six lanes to four lanes at cochran av ... resulting in enormous traffic jam during the morning rush hour going north ... and also changed from six lanes to four lanes in south san jose (about at hiway 85 merge) resulting in enormous traffic jam going south in the evening.
it was common at the time to name lab. for closest post office ... when there wasn't any other designation.
that wasn't the problem. however, I happened to be in Washington DC with the kids during spring break (the week before scheduled opening of STL). There were a number of demonstrations on the steps of the capital by "coyote", a san francisco working lady's association.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: UK issues Turning apology (and about time, too) Newsgroups: alt.folklore.computers Date: Thu, 17 Sep 2009 08:35:30 -0400jmfbahciv <jmfbahciv@aol> writes:
it wasn't the buyers qualifications ... it was unregulated loan originators ... that weren't worried about buyer's qualifications at all ... getting access to enormous source of funds.
the thing in the middle that enabled the whole thing was rating agencies giving triple-A ratings to (mortgage backed) toxic CDOs (without that enabling ... rather than tens of trillions in funds ... there would possibly been barely hundreds of millions available to unregulated mortgage originators). SEC was inactive during the period ... even w/o other oversight authority ... there was additional burden placed on SEC with regard to the rating agencies in Sarbanes-Oxley.
regulated depository institutions got into trouble with having huge amounts of such toxic CDOs ... because 1999 repeal of Glass-Steagall allowed the regulated depository institutions to have unregulated investment banking operations buying things and carrying them offbook (end of last year there was something about the four largest regulated depository institutions having something like five trillion in toxic CDOs being carried off book ... courtesy of their unregulated investment banking operations).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: OSS's Simple Sabotage Field Manual Newsgroups: alt.folklore.computers Date: Thu, 17 Sep 2009 16:25:32 -0400Alexander Schreiber <als@usenet.thangorodrim.de> writes:
... it is possible to use the same URL w/o the "s" (aka just plain
http:).
http://svn.cacert.org/CAcert/CAcert_Inc/Board/oss/oss_sabotage.html
i've been using the reference about the whole certificate infrastructure
being "comfort" operations (way too many holes to be considered "secure"
operations ... just enuf of a facade to make people feel comfortable
about the mechanism). misc. past ssl digital certificate posts
https://www.garlic.com/~lynn/subpubkey.html#sslcerts
in various security & browser venues ... there have been lots of discussions about what should browser interface actually do. there have been cases where blatently incorrect certificates have resulted in simple error messages that users become accustomed to ignoring.
current firefox it is possible to click "I understand the risks", then click "add exception", then click "get certificate", then click "view", then uncheck "permanently store this exception" (i.e. only do it temporarily), and then click "confirm security exception".
it doesn't actually add the root certificate to list of trusted ... it does temporarily accept the particular SSL certificate for the current browser invokation.
while I have no evidence that the document is a spoof ... the contents appear to so closely resemble standard corporate behavior ... I have a little difficulty believing it is actually from 44 ... and not some current corporate manual.
CA cert home page:
http://www.cacert.org/
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Mainframe Hall of Fame: Three New Members Added To: <ibm-main@bama.ua.edu> Date: Thu, 17 Sep 2009 17:01:26 -0400Mike.Myers@PCMH.COM (Mike Myers) writes:
previously referenced URL with pictures and blurb about
"silicon valley lab"
http://www.ajnordley.com/IBM/Air/SVL/
also from above:
Formerly known as "Santa Teresa Lab" (STL), IBM's SVL, nestled in the
country side just south of the foot hills at the north end of the Coyote
Valley in south San Jose, employs 1,300 people, and is where much of the
software for IBM systems is developed.
... snip ...
wiki page
https://en.wikipedia.org/wiki/Coyote_Valley
when tandem growth was at its height, they took option on the open field
on the other side of santa teresa blvd (north of bailey ave) ... to
build a large campus type location ... and then things took a downturn
and it never happened. both tandem and apple had plans in the 70s moving
major operations into coyote valley.
http://lomaprieta.sierraclub.org/lp0103_Disasters.html
from above:
• Coyote Valley in south San Jose (still being waged by the chapter). In
1983 the San Jose City Council approved a 548-acre industrial park for
Tandem Computers, which, the LP reported, "in effect, opens up the
entire 5,000-acre Coyote Valley for development." (The Tandem facility
was not built.)
... snip ...
apple and others had plans at various times in expanding into coyote
valley.
http://www.sanjoseca.gov/coyotevalley/index.html
article from March 1999:
http://findarticles.com/p/articles/mi_hb5553/is_199903/ai_n22390270/
from above:
Mar. 3 -- Sixteen years after former Silicon Valley up-and-comers such
as Tandem Computers Inc., Verbatim Corp. and Apple Computer Inc. said
they were headed to San Jose's Coyote Valley, Cisco Systems Inc. on
Tuesday formally announced its intention to do likewise.
... snip ...
slightly related tandem drift ... past post mentioning
celebration for Jim Gray last year:
https://www.garlic.com/~lynn/2008p.html#27 Father of Financial Dataprocessing
When Jim left for Tandem ... Jim wanted me to take over some number of
his activities at IBM ... including things like consulting with the IMS
group and interfacing to early relational database customers (some
references in the above post, including references to old email from the
period). A recent post discussing some of the subject
https://www.garlic.com/~lynn/2009n.html#3 Hacker charges also an indictment on PCI, expert says
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: UK issues Turning apology (and about time, too) Newsgroups: alt.folklore.computers Date: Fri, 18 Sep 2009 08:50:21 -0400Anne & Lynn Wheeler <lynn@garlic.com> writes:
from today ..
SEC proposes flash ban; takes aim at credit rating agencies
http://www.finextra.com/fullstory.asp?id=20514
from above:
Separately, the watchdog has voted to bolster oversight of credit
ratings agencies. The move is designed to reduce conflicts of interest
at the firms, which have been criticized for contributing to the
subprime mortgage crisis and subsequent financial meltdown.
... snip ...
congress had hearings on the rating agencies a year ago ... where several testified that the rating agencies were "selling" triple-A ratings (on toxic CDOs), even when both the rating agencies and the sellers knew the things weren't worth triple-A ratings. Testimony said that the seeds for this was sown in the early 70s when the rating agencies switched from the buyers paying for the ratings to the sellers paying for the ratings (opening things up for conflict of interest).
It is not clear that there is any substantive change.
misc. posts mentioning that interactive data bought "pricing services" division from rating agencies in the early 70s (about the time they switched from buyers paying for the ratings to the sellers paying for the ratings). disclaimer ... i interviewed with interactive data in the late 60s (but didn't join) ... they were one of the online interactive (virtual machine) cp67 time-sharing services formed ... and quickly moved up the value chain offering financial information on the service. Nearly a year ago, there was some news reference about gov. involving interactive data in helping evaluate toxic CDOs (this was when treasury lobbied congress for TARP funds using justification that the money would all go to buying toxic CDOs, there have been recent references, that treasury never used TARP funds for purpose that they were appropriated for)
https://www.garlic.com/~lynn/2009.html#21 Banks to embrace virtualisation in 2009: survey
https://www.garlic.com/~lynn/2009.html#31 Banks to embrace virtualisation in 2009: survey
https://www.garlic.com/~lynn/2009.html#32 What are the challenges in risk analytics post financial crisis?
https://www.garlic.com/~lynn/2009.html#42 Lets play Blame Game...?
https://www.garlic.com/~lynn/2009.html#52 The Credit Crunch: Why it happened?
https://www.garlic.com/~lynn/2009.html#77 CROOKS and NANNIES: what would Boyd do?
https://www.garlic.com/~lynn/2009.html#79 The Credit Crunch: Why it happened?
https://www.garlic.com/~lynn/2009b.html#38 A great article was posted in another BI group: "To H*** with Business Intelligence: 40 Percent of Execs Trust Gut"
https://www.garlic.com/~lynn/2009b.html#49 US disaster, debts and bad financial management
https://www.garlic.com/~lynn/2009b.html#53 Credit & Risk Management ... go Simple ?
https://www.garlic.com/~lynn/2009b.html#78 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#1 Audit II: Two more scary words: Sarbanes-Oxley
https://www.garlic.com/~lynn/2009e.html#15 The background reasons of Credit Crunch
https://www.garlic.com/~lynn/2009e.html#53 Are the "brightest minds in finance" finally onto something?
https://www.garlic.com/~lynn/2009e.html#70 When did "client server" become part of the language?
https://www.garlic.com/~lynn/2009f.html#41 On whom or what would you place the blame for the sub-prime crisis?
https://www.garlic.com/~lynn/2009f.html#49 Is the current downturn cyclic or systemic?
https://www.garlic.com/~lynn/2009h.html#40 Analysing risk, especially credit risk in Banks, which was a major reason for the current crisis
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: UK issues Turning apology (and about time, too) Newsgroups: alt.folklore.computers Date: Fri, 18 Sep 2009 09:38:04 -0400Anne & Lynn Wheeler <lynn@garlic.com> writes:
... of course, less than trillion in TARP would hardly make a dent in
possibly $27T in toxic CDOs. one of the issues was that there were a a
couple thousand people executing extremely risky transactions (w/o
regard to the institution or systemic risk or the threat to the
country's or world economy), purely for personal beneift
... compensation/bonus was possibly some percent of the size of the
(immediate) transaction w/o any consideration for consequences of such
transactions.
Evil Wall Street Exports Boomed With 'Fools' Born to Buy Debt
https://www.bloomberg.com/news/articles/2008-10-27/evil-wall-street-exports-boomed-with-fools-born-to-buy-debt
a few old posts mentioning TARP
https://www.garlic.com/~lynn/2008r.html#61 The vanishing CEO bonus
https://www.garlic.com/~lynn/2008s.html#32 How Should The Government Spend The $700 Billion?
https://www.garlic.com/~lynn/2008s.html#33 Garbage in, garbage out trampled by Moore's law
https://www.garlic.com/~lynn/2008s.html#35 Is American capitalism and greed to blame for our financial troubles in the US?
https://www.garlic.com/~lynn/2008s.html#41 Executive pay: time for a trim?
https://www.garlic.com/~lynn/2009.html#73 CROOKS and NANNIES: what would Boyd do?
https://www.garlic.com/~lynn/2009.html#80 Are reckless risks a natural fallout of "excessive" executive compensation ?
https://www.garlic.com/~lynn/2009b.html#25 The recently revealed excesses of John Thain, the former CEO of Merrill Lynch, while the firm was receiving $25 Billion in TARP funds makes me sick
https://www.garlic.com/~lynn/2009b.html#30 The recently revealed excesses of John Thain, the former CEO of Merrill Lynch, while the firm was receiving $25 Billion in TARP funds makes me sick
https://www.garlic.com/~lynn/2009b.html#35 The recently revealed excesses of John Thain, the former CEO of Merrill Lynch, while the firm was receiving $25 Billion in TARP funds makes me sick
https://www.garlic.com/~lynn/2009b.html#41 The subject is authoritarian tendencies in corporate management, and how they are related to political culture
https://www.garlic.com/~lynn/2009b.html#45 The recently revealed excesses of John Thain, the former CEO of Merrill Lynch, while the firm was receiving $25 Billion in TARP funds makes me sick
https://www.garlic.com/~lynn/2009b.html#49 US disaster, debts and bad financial management
https://www.garlic.com/~lynn/2009b.html#57 Credit & Risk Management ... go Simple ?
https://www.garlic.com/~lynn/2009b.html#59 As bonuses...why breed greed, when others are in dire need?
https://www.garlic.com/~lynn/2009c.html#10 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#11 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#16 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009d.html#73 Should Glass-Steagall be reinstated?
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Blast from the Past - 60 years of cryptography Newsgroups: alt.folklore.computers Date: Mon, 21 Sep 2009 09:32:13 -0400SLIDESHOW: CIO Blast from the Past - 60 years of cryptography 2009 marks 60 years of computer cryptography and CIO takes a tour of the history of secure communication
http://www.cio.com.au/article/319119/slideshow_cio_blast_from_past_-_60_years_cryptography
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: COBOL Celebrates 50 Years Newsgroups: alt.folklore.computers Date: Mon, 21 Sep 2009 09:37:16 -0400COBOL turns 50 - a-z of programming languages, COBOL, programming
from above:
"The language used to power most of the world's ATMs, COBOL, is turning 50."
... snip ...
slightly related
https://www.garlic.com/~lynn/2008p.html#27 Father of Financial Dataprocessing
recent posts mentioning above:
https://www.garlic.com/~lynn/2009l.html#20 Cyber attackers empty business accounts in minutes
https://www.garlic.com/~lynn/2009l.html#29 IBM launches integrated mainframe packages for payments, data warehousing and SOA
https://www.garlic.com/~lynn/2009l.html#57 IBM halves mainframe Linux engine prices
https://www.garlic.com/~lynn/2009l.html#64 Hacker charges also an indictment on PCI, expert says
https://www.garlic.com/~lynn/2009m.html#78 ATMs by the Numbers
https://www.garlic.com/~lynn/2009n.html#3 Hacker charges also an indictment on PCI, expert says
https://www.garlic.com/~lynn/2009n.html#19 Mainframe Hall of Fame: Three New Members Added
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Mon, 21 Sep 2009 17:30:50 -0400hancock4 writes:
there is whole series of RFCs looking at the week-by-week transition of IMPs (& host protocol) to TCP/IP ... starting Dec. 1982 with RFC832 (series: "Who Talks TCP?"). RFC832 has a little over 300 hosts. In the arpanet there was little ambiquity with IMPs being the network nodes when then had "hosts" hung off the IMPs. There were earlier ARPA/DDN references predicting 100 IMPs (network nodes) and more than 256 hosts by ye82.
this references that in 1983, 68 of the 113 existing "nodes" went to
MILNET:
http://www.thocp.net/reference/internet/internet2.htm
there is a series from the 75 time-frame "survey of New-Protocol Telnet servers": RFC703, July, 1975 which lists 43 hosts.
this reference mentions 98 nodes on the ARPAnet in 1976 (but may
actually be referring to "hosts").
http://www.cs.ucsb.edu/~almeroth/classes/F04.176A/homework1_good_papers/jay-akkad.html
43->98 hosts implies possibly doubling in twelve (or possibly 18; mid-75 to ye76?) month period. doesn't necessarily imply increase in number of locations
hobbes' internet timeline
http://home.utah.edu/history.html
1981 BITNET, the "Because Its Time (There) NETwork"
- Started as a cooperative network at the City University of New York.
- Provides electronic mail and listserv servers to distribute
information.
- Unlike USENET, where client s/w is needed, electronic mail is the
only tool necessary.
CSNET (Computer Science NETwork) comes into being providing a dial-up
capability to electronic mail. Many universities feeling left out
of ARPANET, join CSNET.
... snip ...
reference to sjr connecting to csnet fall of '82
https://www.garlic.com/~lynn/internet.htm#email821022
search engine for "csnet 1982 nodes arpanet" turns up an acm.org entry ... clicking on the URL doesn't mention this ... but the search engine blurb for the URL has this little tidbit:
sites until late in 1982, becomes available for CSNET member .... An ARPANET node (IMP) costs roughly. $107000 annually in 1983 (flat rate, no additional ...
... snip ...
csnet & univ. bitnet connections were significantly lower (bitnet & earn links had corporate subsidy, further lowering cost of entry for educational institutions).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Mon, 21 Sep 2009 18:14:28 -0400Patrick Scheible <kkt@zipcon.net> writes:
take a look at the telnet survey for jul75
Host Number Host (Oct) (Dec) Name 101 65 UCLA-CCN 201 129 UCLA-CCBS 102 66 SRI-AI 3 3 UCSB-MOD75 4 4 UTAH-10 305 197 BBN-TENEXA 106 70 MIT-DMS 206 134 MIT-AI 306 198 MIT-ML 7 7 RAND-RCC 107 71 RAND-ISD 10 8 SDC-LAB 11 9 HARV-10 12 10 LL-67 112 74 LL-TX-2 13 11 SU-AI 16 14 CMU-10B 116 78 CMU-10A 17 15 I4-TENEX 217 143 I4B-TENEX 20 16 AMES-67 25 21 LLL-RISOS 126 86 USC-ISI 226 150 USC-ISIB 27 23 USC-44 327 215 USC-ECL 32 26 SDAC-44 34 28 ARPA-DMS 37 31 CCA-TENEX 40 32 PARC-MAXC 43 35 UCSD-CC 344 228 HAWAII-500 52 42 LONDON 53 43 OFFICE-1 54 44 MIT-MULTICS 55 45 SCI-TENEX 56 46 RUTGERS-10 61 49 BBN-TENEXB 361 241 BBN-TENEX 162 114 BBN-TENEXD 364 244 USC-ISIC 67 55 ANL 70 56 SUMEX-AIM... snip ...
there is the lincoln labs (ll-67) (cp67) still listed(?)
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Signature specification without certificates Newsgroups: sci.crypt Date: Mon, 21 Sep 2009 18:06:49 -0400"James H. Markowitz" <noone@nowhere.net> writes:
The certificate-oriented specifications from the period typically resulted in a 100-times increase in payment transaction payload size. Some just worked over the internet ... stripping off the digital certificate at the internet boundary and just including a bit in the actual payment transaction indicating that the digital certificate had validated the digital signature. There was pilot effort that if that bit was turned on, the "interchange fee" for the transaction was lower (cost the merchant less money). There was then report of the number of payment transactions with the bit turned on and it could be proved that no digital signatures or digital certificates were involved.
It was futher confounded by the fact that the financial institutions were registering their customers and issuing the digital certificates (as well as retaining all the information that went into the digital certificate).
A digital certificate oriented payment transaction was then appending
and transmitting back to the customer's financial institution, a copy of
the digital certificate (even if it only travelled part way); when the
customer's financial institution had retained all that information (the
digital certificates not only resulted in 100-times increase in payment
transaction payload size, they were also redundant and superfluous).
https://www.garlic.com/~lynn/subpubkey.html#bloat
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Continous Systems Modelling Package Newsgroups: alt.folklore.computers Date: Mon, 21 Sep 2009 22:16:41 -0400re:
mention of nlm in ...
tymshare tymnet article form
Future Networks, infotech state of the art conference, london, 14-15nov1977
http://archive.computerhistory.org/resources/text/Tymshare/tymshare.future_networks.1977.102640323.pdf
from above:
In November, 1971, TYMNET was fully deployed and operational, a
50-node net serving 5 host computers for Tymshare, Inc. In February,
1972, the National Library of Medicine put the first non-Tymshare host
on the net, an IBM 370/155 with a medical data base. Since then,
TYMNET has evolved far beyond its original design goals to become the
largest value added network, serving about 25,000 users a day. It is
the only international value added network currently operating.
... snip ...
misc. other recent posts mentioning Tymshare
https://www.garlic.com/~lynn/2009j.html#79 Timeline: The evolution of online communities
https://www.garlic.com/~lynn/2009l.html#14 August 7, 1944: today is the 65th Anniversary of the Birth of the Computer
https://www.garlic.com/~lynn/2009l.html#16 August 7, 1944: today is the 65th Anniversary of the Birth of the Computer
https://www.garlic.com/~lynn/2009l.html#52 August 7, 1944: today is the 65th Anniversary of the Birth of the Computer
https://www.garlic.com/~lynn/2009n.html#9 Existence of early 360 software ( was Re: Continous Systems Modelling Packa
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Mon, 21 Sep 2009 22:36:50 -0400Patrick Scheible <kkt@zipcon.net> writes:
where arpanet had more "hosts" than IMPs (nodes) ... (tymshare's) tymnet
had larger number of their (tymnet) network nodes ... but fewer hosts
https://www.garlic.com/~lynn/2009n.html#27 Continous Systems Modelling Package
above references this paper ...
http://archive.computerhistory.org/resources/text/Tymshare/tymshare.future_networks.1977.102640323.pdf
tymnet wiki page
https://en.wikipedia.org/wiki/Tymnet
above mentions Varian minicomputers. random virtual machine trivia, Varian had cp/67 system for doing design work ... some of the engineers showed up later at LSI Logic ... and using VM/370 hosts for engineering design.
Varian wiki page ...
https://en.wikipedia.org/wiki/Varian_Associates
LSI Logic wiki page ..
https://en.wikipedia.org/wiki/LSI_Corporation
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Tue, 22 Sep 2009 11:39:22 -0400Patrick Scheible <kkt@zipcon.net> writes:
just for the fun of it ... i did grep of all RFCs using some of the host names from jul75 telnet survey RFC.
there is RFC751 dated 10Dec78 which is an email survey. neither telnet survey nor the email survey actually claim that they list all known hosts (43 for telnet survey & 92 for email survey) ... however, at least the email survey lists hosts in several categories ... including all those that didn't respond (implying that they attempted to contact all hosts).
it would seem that number of hosts slightly more than doubled between
Jul75 and dec78 ... and then slightly more than tripled between dec78
and dec82 (to something like 300 hosts).
AFWL AMES-67 ANL ARPA-DMS BBN-TENEX BBN-TENEXA BBN-TENEXB BBN-TENEXD
BBN-TENEXE BBN-UNIX BNL CCA-SDMS CCA-SPEECH CCA-TENEX CCTC CMU-10A
CMU-10B CMU-10D CMU-CMMP CTO-DDS DEC-MARLBORO DTI DTNSRDC EGLIN FNWC
GUNTER-UNIX HARV-10 I4-TENEX I4B-TENEX ILL-UNIX ISI-SPEECH11 LBL
LBL-UNIX LL LL-11 LL-ASG LL-XN LLL-COMP LLL-MFE LONDON LONDON-VDH
MIT-AI MIT-DMS MIT-MC MIT-ML MIT-MULTICS MIT-XX MOFFET-ARC NADC NBS-10
NBS-UNIX NCSC NDRE NOSC-CC NOSC-SDL NOSC-SECURE1 NSWC-WO NTIA-ITS NUSC
NUSC-NPT NWC NYU OFFICE-1 OFFICE-2 PARC-MAXC PARC-MAXC2 PENT-UNIX
RADC-MULTICS RADC-TOPS20 RADC-XPER RAND-RCC RAND-UNIX RUTGERS SDAC-44
SDAC-UNIX SRI-KA SRI-KL SRI-UNIX SU-AI SUMEX-AIM UCLA-ATS UCLA-CCN
UCLA-SECURITY USC-ECL USC-ISI USC-ISIB USC-ISIC USC-ISIE UTEXAS
WHARTON WPAFB WPAFB-AFAL
... snip ...
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Tue, 22 Sep 2009 11:45:33 -0400Anne & Lynn Wheeler <lynn@garlic.com> writes:
... and much of the growth in number of hosts between jul75 and decl78 seems to be additional connected hosts at existing network nodes (as opposed to additional hosts at new network nodes).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Tue, 22 Sep 2009 13:19:58 -0400Eric Chomko <pne.chomko@comcast.net> writes:
for the fun of it ... i include RFC listed by month published ...
https://www.garlic.com/~lynn/rfcietff.htm
click on "Date" in the RFCs listed by section.
there are a bunch RFCs/month in 71-73 time-frame and then drops off and doesn't really pick back up until the early 90s.
when i started my index ... i would also do some sanity checking regarding listed RFCs in standardization process (STD1) and found a bunch of inconsistencies ... for a while, Postel would carry the list as section "6.10" in STD1. The inconsistencies were eventually cleaned up over time.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Tue, 22 Sep 2009 19:36:23 -0400Al Kossow <aek@bitsavers.org> writes:
+----------------------------------------------------------+ | You have reached what *USED* *TO* *BE* ftp.nisc.sri.com | +----------------------------------------------------------+ +----------------------------------------------------------+ | This site no longer supports NIC related services | | This site no longer maintains any RFC or IETF archives | | This site no longer supports anonymous FTP service | +----------------------------------------------------------+ +----------------------------------------------------------+ | If you are a warm body, you may want to try connecting | | to the FTP server at one of the following sites instead: | | DS.INTERNIC.NET NIS.NSF.NET | | NISC.JVNC.NET VENERA.ISI.EDU | | WUARCHIVE.WUSTL.EDU SRC.DOC.IC.AC.UK | | FTP.CONCERT.NET FTP.SESQUI.NET | +----------------------------------------------------------+ +----------------------------------------------------------+ | If you are a program (like archie), please remove this | | site from your database of FTP sites (as if "you" will | | actually understand and heed this message) | +----------------------------------------------------------+ +----------------------------------------------------------+ | Lack of FTP service signing off. Over and out... | +----------------------------------------------------------+... snip ...
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Tue, 22 Sep 2009 23:53:01 -0400Walter Bushell <proto@panix.com> writes:
ISO had the "OSI Model" ... and requirement that (international networking) standardization work had to conform to the "OSI Model" (sometimes referred to as simply OSI).
I was involved in taking HSP (high-speed protocol) to ANSI (ISO chartered standards organization in the US) X3S3.3 (responsible for standards related to level 3 & level 4 in the OSI Model)
Is was rejected because there three places where it didn't conform to the OSI model:
1) it supported internetworking protocol ... a non-existent layer in the "OSI model" (somewhere between level 3, networking & level 4, transport).
2) it went directly from level 4, transport to LAN MAC interface, bypassing the level3/level4 interface.
3) it went directly to LAN MAC interface, LAN MAC is something that didn't exist in the OSI Model (LAN MAC interface sits somewhere in the middle of level 3, and subsumes some of the level 3, networking function, defined in the OSI Model.
misc. past posts mentioning HSP (and sometimes X3S3.3)
https://www.garlic.com/~lynn/subnetwork.html#xtphsp
there were other comments about ISO not actually requiring any working implementation for a standard ... compared to IETF which has required at least two interoperable implementations before standardization.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Wed, 23 Sep 2009 10:40:05 -0400"Dave Wade" <g8mqw@yahoo.com> writes:
a big reason was that OSI still represented the closed VAN networks of the 70s (aka the recent Tymnet reference) ... each operation would offer their own closed networks ... that didn't interoperate (aka have a "internetworking" layer that might interconnect all networks). High prices and closed infrastructure sort of went hand-in-hand.
as previously referenced ... ISO could have final standardization before any implementation was even attempted (not only didn't know about whether implementations were interoperable ... but didn't know if it was even implementable) ... in contrast with IETF which required two (different) interoperable implementations before standardization.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Cybersecurity Today: The Wild, Wild West Newsgroups: alt.folklore.computers Date: Wed, 23 Sep 2009 19:56:02 -0400Cybersecurity Today: The Wild, Wild West
from above:
"We're the most vulnerable nation on the Earth because we're the most dependent," John "Mike" McConnell, former director of national intelligence and a senior vice president at Booz Allen Hamilton, says at a conference organized by the Security Innovation Network.
... snip ...
Anne had been con'ed in to doing a stint in charge of (mainframe)
loosley-coupled (cluster) architecture in POK. While there, she
came up with Peer-Coupled Shared Data architecture
https://www.garlic.com/~lynn/submain.html#shareddata
which except for IMS hot-standby ... didn't see any uptake until sysplex. this contributed to her not staying long in the position ... and then leaving to do a gig at SBS. SBS was eventually dissolved and bits & pieces sold off. BAH picked up the SBS building in Tysons.
a couple yrs ago we had opportunity to have meeting at BAH in conference room on the same flr where her office used to be. Although BAH had gutted and remodeled the interior ... "Mike's" office was almost exactly where her's had been.
misc. past posts mentioning internet & wild, wild west:
https://www.garlic.com/~lynn/2000g.html#39 Could CDR-coding be on the way back?
https://www.garlic.com/~lynn/2001m.html#27 Internet like city w/o traffic rules, traffic signs, traffic lights and traffic enforcement
https://www.garlic.com/~lynn/2001m.html#28 Internet like city w/o traffic rules, traffic signs, traffic lights and traffic enforcement
https://www.garlic.com/~lynn/2001m.html#29 Internet like city w/o traffic rules, traffic signs, traffic lights and traffic enforcement
https://www.garlic.com/~lynn/2001m.html#30 Internet like city w/o traffic rules, traffic signs, traffic lights and traffic enforcement
https://www.garlic.com/~lynn/2001m.html#31 Internet like city w/o traffic rules, traffic signs, traffic lights and traffic enforcement
https://www.garlic.com/~lynn/2002.html#24 Buffer overflow
https://www.garlic.com/~lynn/2002.html#26 Buffer overflow
https://www.garlic.com/~lynn/2002f.html#24 Computers in Science Fiction
https://www.garlic.com/~lynn/2003b.html#62 Storing digital IDs on token for use with Outlook
https://www.garlic.com/~lynn/2003i.html#17 Spam Bomb
https://www.garlic.com/~lynn/2003j.html#34 Interrupt in an IBM mainframe
https://www.garlic.com/~lynn/2003n.html#20 which CPU for educational purposes?
https://www.garlic.com/~lynn/2004i.html#16 New Method for Authenticated Public Key Exchange without Digital Ceritificates
https://www.garlic.com/~lynn/2004k.html#32 Frontiernet insists on being my firewall
https://www.garlic.com/~lynn/2004o.html#53 360 longevity, was RISCs too close to hardware?
https://www.garlic.com/~lynn/2005g.html#21 Protocol stack - disadvantages (revision)
https://www.garlic.com/~lynn/2007c.html#30 Securing financial transactions a high priority for 2007
https://www.garlic.com/~lynn/2007c.html#32 Securing financial transactions a high priority for 2007
https://www.garlic.com/~lynn/2007c.html#43 Securing financial transactions a high priority for 2007
https://www.garlic.com/~lynn/2007h.html#32 sizeof() was: The Perfect Computer - 36 bits?
https://www.garlic.com/~lynn/2007h.html#67 SSL vs. SSL over tcp/ip
https://www.garlic.com/~lynn/2007k.html#48 John W. Backus, 82, Fortran developer, dies
https://www.garlic.com/~lynn/2007m.html#7 nouns and adjectives
https://www.garlic.com/~lynn/2007n.html#15 What if phone company had developed Internet?
https://www.garlic.com/~lynn/2007n.html#16 What if phone company had developed Internet?
https://www.garlic.com/~lynn/2007p.html#67 what does xp do when system is copying
https://www.garlic.com/~lynn/2007r.html#13 What do ATMS and card readers use?
https://www.garlic.com/~lynn/2007r.html#45 Translation of IBM Basic Assembler to C?
https://www.garlic.com/~lynn/2007s.html#34 File sharing may lead to identity theft
https://www.garlic.com/~lynn/2007u.html#87 CompUSA to Close after Jan. 1st 2008
https://www.garlic.com/~lynn/2007v.html#53 folklore indeed
https://www.garlic.com/~lynn/2008.html#37 1975 movie "Three Days of the Condor" tech stuff
https://www.garlic.com/~lynn/2008g.html#26 CA ESD files Options
https://www.garlic.com/~lynn/2008p.html#28 Can Smart Cards Reduce Payments Fraud and Identity Theft?
https://www.garlic.com/~lynn/2008p.html#31 FC5 Special Workshop CFP: Emerging trends in Online Banking and Electronic Payments
https://www.garlic.com/~lynn/2008p.html#72 Alternative credit card network
https://www.garlic.com/~lynn/2008p.html#75 Alternative credit card network
https://www.garlic.com/~lynn/2008r.html#29 What if the computers went back to the '70s too?
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: The Compliance Spectrum...Reducing PCI DSS Scope Date: 23 Sep, 2009 Blog: Information Security NetworkThe Compliance Spectrum...Reducing PCI DSS Scope
from above:
This is an article from the 2nd Quarter of Secure Payments. Recently
people have been asking about how I can state that the use of
end-to-end encryption, tokenization, data vault technologies, and
point to point encryption can reduce the PCI DSS compliance burden
... snip ...
Secure Payments
http://www.securepaymentsmag.com/
...
The issue is that in the current paradigm .... PANs are extremely vulnerable ... just knowing the PAN enables being able to perform fraudulent financial transactions ... besides being extremely vulnerable ... it is also required in large number of business processes that occur at millions of places around the world. As a result, we've frequently commented that even if the planet were buried under miles of (information hiding) encryption, it wouldn't stop (PAN) information leakage.
In the mid-90s, the x9a10 financial standard working group was given
the requirement to preserve the integrity of the financial
infrastructure for *ALL* retail payments (POS, internet, unattended,
debit, credit, stored-value, contact, contactless, mobile phone,
low-value, high-value, transit turnstyle, etc). As part of the effort,
detailed end-to-end threat and vulnerability studies were done ... and
resulted in the x9.59 financial standard ... misc. references
https://www.garlic.com/~lynn/x959.html#x959
Part of the X9.59 financial standard was to slightly tweak the paradigm to remove the PAN as threat/vulnerability. It didn't do anything about trying to hide the PAN ... it just eliminated the ability for crooks knowing the PAN, to perform fraudulent transactions.
Prior to getting invited to participate in X9A10, we had been asked to consult with small client/server startup that wanted to do payment transactions on their server ... the startup had invented this technology called SSL they wanted to use ... the result is now frequently called "electronic commerce". The biggest use of SSL in the world today is hiding PAN information as part of this thing called "electronic commerce". One of the results of X9.59 eliminating the need to hide the PAN ... it also eliminates the major use of SSL in the world today.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Firms failing to treat card data security seriously Date: 23 Sep, 2009 Blog: Financial Crime Risk, Fraud and SecurityFirms failing to treat card data security seriously
In the mid-90s, we were asked to participate in the x9a10 financial
standard working group which had been given the requirement to
preserve the integrity of the financial infrastructure for all retail
payments. The result was x9.59 standard
https://www.garlic.com/~lynn/x959.html#x959
Part of X9.59 standard was to eliminate card data as a vulnerability (slightly tweaked the paradigm so crooks weren't able to use the information for fraudulent financial transactions). One of the observation was that because of the millions of places that card data had to be available for business processes, even if the planet was buried under miles of (information hiding) encrypting, it still wouldn't prevent information leakage.
Credit-card security standards questioned, survey says; IT security
executives say big benefit of PCI is impressing business partners, not
locking down credit-card data
http://www.networkworld.com/news/2009/100909-congress-mainframes.html
Some of PCI is possibly in response to the (originally Cal state) data breach notification legislation. We were tangentially involved when we were called in to help word-smith the cal. state electronic signature legislation. There were organizations involved in the electronic signature legislation that were heavily involved in privacy issues. They had done in-depth consumer privacy surveys and found the number one issue was "identity theft" ... and a major form of "identity theft" was "account fraud" .... crooks harvesting card information and using the obtained information to perform fraudulent transactions (as previously referenced, x9.59 earlier had slightly tweaked the paradigm to eliminate harvesting card information as a vulnerability ... crooks no longer able to use the harvested information to perform fraudulent financial transaction).
There seemed to be impression that there was little being done to counter-act harvesting card information and some anticipation that resulting publicity from breach notification might motivate countermeasures.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Cybersecurity Today: The Wild, Wild West Newsgroups: alt.folklore.computers Date: Thu, 24 Sep 2009 10:16:44 -0400"Chris Burrows" <cfbsoftware@hotmail.com> writes:
lots of past posts regarding C & common software errors
https://www.garlic.com/~lynn/subintegrity.html#overflow
In the 80s, I had done a lot of programming in vs/pascal ... and never experienced any of the software errors in vs/pascal that are common in C (while it isn't impossible in vs/pascal ... it is about as hard to have some of these errors ... as it is hard in C to *NOT* have the errors). Mainframe tcp/ip implementation was done in vs/pascal ... and I know of none of the common length problems (frequent in C) in that implementation.
A couple of above posts:
https://www.garlic.com/~lynn/2002l.html#42 Thirty Years Later: Lessons from the Multics Security Evaluation
https://www.garlic.com/~lynn/2002l.html#44 Thirty Years Later: Lessons from the Multics Security Evaluation
references a paper looking at '74 air force study of multics
http://www.acsac.org/2002/papers/classic-multics.pdf
including finding the (PLI implementation) Multics had no instances of buffer length related software errors
and slightly related, a NASA High Dependability Computing Consortium
workshop (both Jim Gray and I were keynote speakers):
https://web.archive.org/web/20011004023230/http://www.hdcc.cs.cmu.edu/may01/index.html
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Thu, 24 Sep 2009 10:33:08 -0400jmfbahciv <jmfbahciv@aol> writes:
from above:
DOCKMASTER
Unclassified Multics system operated by the US National Security Agency
in Linthicum, MD. 1984-1998. Used as a communications tool among
security researchers, lots of forum activity. See the DOCKMASTER site
history.
... snip ...
and:
https://www.multicians.org/site-dockmaster.html
the above mentions that the DOCKMASTER IMP was hit by lightning in July 1986 and was down for many weeks.
The referenced machine didn't come into existance until after the switch-over to internetworking (and split off of the gov. part). However, the above implies that after the split, IMPs (and original arpanet protocols) continued on for some time (in the gov) ... before they eventually moved to internetnetworking.
Then there is this reference to systems that they used in the 60s:
https://web.archive.org/web/20090117083033/http://www.nsa.gov/research/selinux/list-archive/0409/8362.shtml
I did a lot of work on cp67 as an undergraduate in the 60s ... and would periodically even get requests from the vendor to do certain kinds of changes/enhancements. In retrospect, some of the requests were possibly of the nature to have originated from some of those customers (however, I didn't actually learn about those guys until much later).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: DARPA, at least, has a clue (maybe, sometimes) Newsgroups: comp.arch Date: Thu, 24 Sep 2009 12:27:11 -0400"Del Cecchi" <delcecchiofthenorth@gmail.com> writes:
slightly related recent post in a.f.c.
https://www.garlic.com/~lynn/2009n.html#39 Status of Arpanet/Internet in 1976?
mentions some darpa related institutions using 360/67 in the 60s & 70s (I didn't learn about those guys until much later).
this is reference to some pontificating I was doing in the 70s & 80s ...
that eventually got me in trouble with the disk division (relative
system thruput of disks had declined by an order of magnitude over a
period of 15 yrs):
https://www.garlic.com/~lynn/93.html#31 Big I/O or Kicking the Mainframe out the Door
with similar user workload profile ... the number of users supported by cp67->vm370 increased by about factor of four (about the same as increase in disk thruput) while the processor power increased by nearly a factor of 50.
some executive in the disk division, taking offense, assigned their performance group to refute the statements. after a few weeks, they came back and said that I had actually slightly understated the problem.
part of the issue was that as undergraduate in the 60s ... i started doing dynamic adaptive resource scheduling (sometimes referred to as fairshare scheduler ... because default policy was fair share) and "scheduling to the bottleneck". By the mid-70s, it was becoming apparent that the bottlenecks were changing (increasing processor speed and memory sizes but disk thruput improvements were lagging).
as mentioned in the above ... just taking processor speed and memory size ... a 3081k should have supported a couple thousand users (rather than a couple hundred) ... just using processor thruput measure.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Follow up Newsgroups: comp.protocols.tcp-ip Date: Thu, 24 Sep 2009 14:23:19 -0400Ouyang <ouyangtu@gmail.com> writes:
as part of the effort, there was something called a "payment gateway"
deployed. we had sign-off authority on the webserver to payment gateway
and we mandated some amount of additional features 1) required "SSL"
mutual authentication (which hadn't been implemented prior to that
time), 2) multiple A-record support (i.e. DNS reponds with multiple
IP-address and if the connection attempt fails for the first IP-address,
it cycles thru other "A records", and 3) some number of compensating
procedures. misc. past posts mentioning "payment gateway"
https://www.garlic.com/~lynn/subnetwork.html#gateway
Part of the problem was that payment transaction messages were use to flowing over a circuit-based infrastructure ... just remapping to packets & the internet, didn't provide the same level of service. An example is that "merchant" trouble desk (merchant having trouble) is expected to do 1st level problem determination within five minutes. Early in trial deployment of the "payment gateway" there was a problem/trouble call that was investigated for three hrs and closed as NTF (no trouble found). There were a lot of implicit diagnostic processes that were lost in move from circuit-based infrastructure to the internet ... and we had to develop compensating processes (new diagnostic and fault isolation operations).
Although, we didn't have sign-off authority on the browser/server side of the operations ... I suggested several times that the browser also include multiple A-record (whether http or https). For instance, a major early adopter was doing national TV advertisements on Sunday NFL football ... and was antificapting a lot of clicks during half-time. However, one of their ISPs (at the time) was in the habit of taking down routers for service on sunday. Even tho they had multiple links to different places in the internet (increased availability) ... multiple-A record support in the browser would be required to get through (if their major ISP connection was down).
Anyway, the browser group responded that multiple A-record support was too advanced and wouldn't do it. I then provided them with example FTP & telnet client (multiple A-record) code from 4.3 RENO. It still took another year to get multiple A-record support into the browser.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: DARPA, at least, has a clue (maybe, sometimes) Newsgroups: comp.arch Date: Fri, 25 Sep 2009 00:02:12 -0400"Del Cecchi" <delcecchiofthenorth@gmail.com> writes:
undergraduate at the univ ... most of the workload was batch & so ran os/360 and the 360/67 as 360/65 for most of the time (I was able to run cp67 a little mostly late weekend nights). I had added ASCII/TTY terminal support to cp67.
I was also responsible for os/360, hasp, etc support at the univ. I then added TTY & 2741 terminal support to HASP ... as well as interactive editor ... implementing the CMS editor command syntax in HASP (time-frame was OS/360 MVT18). Allowed editing and batch jog submission.
Univ. didn't have any 2260s ... however, original cp67 2741 & 1052 support was done in such a way, tricks of programming 2702 controller, that it did automatic terminal type identification. When I added, TTY support (both cp67 and later HASP), i tried to do the same thing. This worked for hardwired lines ... but was problem with dial-up using common base number for rotary pool (the problem was a short cut in the 2702 hardware implementation that hardwired the line-speed for each port; 2741 & 1052 were fine because they were same line-speed ... but TTY was different).
This was somewhat motivation behind univ. starting a clone controller project; reverse engineer mainframe channel interface, build channel interface board for Interdata/3 and program Interdata/3 to emulate 2702 controller, with addition of being able to do agile/dynamic line-speed. Four of us got written up & blamed for clone controller product. orignally sold under interdata name and later under perkin/elmer logo ... at least thru much of the 80s, a lot went into gov. accounts. The implementation started out with interdata/3 handling both the channel interface and the line scanner. This was later extended to cluster with interdata/4 handling the channel interface and multiple interdate/3s handling the line scanner function.
the univ. had also gotten a 2250mod1 (channel attach) ... and I also played with cms editor supporting 2250.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Fri, 25 Sep 2009 09:47:18 -0400jmfbahciv <jmfbahciv@aol> writes:
corporations donated resources to NSFNET backbone (and other education networks, significantly in excess of what was paid for). This was targeted at creating incubator for bandwidth hungry apps ... and the prohibitions against commercial use ... was as much to prevent commercial revenue from bleeding off into educational networks, as any other reason. In that sense it worked.
misc. past posts mentioning NSFNET
https://www.garlic.com/~lynn/subnetwork.html#nsfnet
as other past references, besides the organizational issues with scaling up the closed arpanet infrastructure ... the arapnet protocols were starting to experience scale-up issues by the late 70s. I remember late 70s comments that arpanet would have sporadic periods where the arpanet links were nearly totally saturated with administrative traffic (exchanging information about what nodes and routes were up ... and which way to route traffic).
internet backbone ran into something like that in the mid-90s (of course the scale-up size was several orders of magnitude larger than arpanet from a couple decades earlier).
we had been called in to consult with small client/server startup that
wanted to do payment transactions on their server ... and they had
invented this technology called "SSL" they wanted to use; the result
is now frequently called "electronic commerce". As part of the effort
we deployed this thing called "payment gateway" ... some past posts
https://www.garlic.com/~lynn/subnetwork.html#gateway
part of the payment gateway was lots of availability ... including
doing HA/CMP configuration ... misc. past posts having done HA/CMP
product
https://www.garlic.com/~lynn/subtopic.html#hacmp
in fact, two people at the startup responsible for the "commerce server"
had previously been involved in our HA/CMP activity ... mentioned
in this Jan92 meeting in Ellison's conference room
https://www.garlic.com/~lynn/95.html#13
part of availability was multiple links into different places in the internet backbone. Initially I started out planning on advertising (routed) alternate routes for servers (multi-home) ip-addresses. However, in the period of the deployment, internet backbone announced transition to hierarchical routing. As a result ... my only fall-back was to multiple A-record ... ip-addresses and routes didn't change ... just that there were multiple A-records (ip-addresses) for the payment gateway URL.
recent post (in tcp-ip n.g.) discussing getting multiple A-record
support implemented:
https://www.garlic.com/~lynn/2009n.html#41
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Follow up Newsgroups: comp.protocols.tcp-ip Date: Fri, 25 Sep 2009 09:58:05 -0400David Schwartz <davids@webmaster.com> writes:
one of the things was TCP session involves a minimum of 7 packet exchange ... and keeps FINWAIT list for dangling session packets. TCP session were assumed to be long-lived ... and session close was relatively infrequent activity with FINWAIT list very short. As a result, there was linear search of the FINWAIT list for incoming packets.
HTTP behavior use of TCP/IP ... was more packet-like (UDP) than session-like (TCP) ... and loaded webservers were starting to see thousands on the FINWAIT list ... and spending 95% of processor time doing FINWAIT list search. Big websites couldn't add machines fast enough to handle the processing requirement. It took a little time for vendors to come out with new release that completely redid FINWAIT list handling and significantly reduced that overhead.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Fri, 25 Sep 2009 18:46:03 -0400a little more x-over from post in thread
regarding tymnet:
HISTORICAL PERSPECTIVE
In the late 1960s, two networks were developed which laid the
groundwork for all networks to follow. They were the ARPAnet, and
TYMNET. The ARPAnet was sponsored by the United States Department of
Defense as an experiment in computer communications.
Its purpose was to tie together many different kinds of large
computers on many different university campuses. A variety of
simultaneous experiments could then be carried out to test the
feasibility of sharing data base, hardware, and software among the
universities.
50 kilobit lines and packet switching were used to move the
data. Since low speed terminal support was not a consideration and
since the lines were lightly loaded, the inefficiencies of packet
switching did not matter. Network control was distributed among the
nodes, with each node having global knowledge of the net. Some
standard host interfaces were developed and many independent teams of
graduate students successfully modified their machines to attach
them to the net. The ARPAnet was quite successful in achieving its
original goals. It became the most widely studied and publiczed
network.
TYMNET developed quite differently. Its primary purpose was to
interface large numbers of low speed terminals to a relatively small
number of timeshared computers operated by Tymshare, Inc. Most of
these terminals were full duplex and interacted with the computers
character by character. Each character was echoed from either the
network or the computer according to what the user was doing. Echo
control had to pass back and forth between network and computer very
smoothly to retain the flexible typing characteristics of the full
duplex terminal. Finally, since this was to operate in a commercial
environment, it had to be efficient and low cost. That ruled out
packet switching and 50 kilobit lines.
A scheme called virtual circuit switching was invented in which the
path that the user's data was to follow was determined when the user
logged on. This path was called the virtual circuit because of its
analogy with a telephone circuit. Data following that circuit does not
have to carry routeing information with it. Furthermore, data from
many users can share the same physical record. The overhead of
checksums and record headers can be spread over many small
users. Finally, since flow control operates node to node rather than
circuit end to circuit end, there is no need for the recipient of data
to send back a message to the sender that it is all right to send more
data. This scheme proved to be so efficient that it is possible to
serve up to 40 low speed (10 to 30 character per second) interactive
terminals on one 2400 bit per second line.
... snip ...
re:
https://www.garlic.com/~lynn/2009n.html#24 Status of Arpanet/Internet in 1976?
https://www.garlic.com/~lynn/2009n.html#25 Status of Arpanet/Internet in 1976?
https://www.garlic.com/~lynn/2009n.html#28 Status of Arpanet/Internet in 1976?
https://www.garlic.com/~lynn/2009n.html#29 Status of Arpanet/Internet in 1976?
https://www.garlic.com/~lynn/2009n.html#30 Status of Arpanet/Internet in 1976?
https://www.garlic.com/~lynn/2009n.html#31 Status of Arpanet/Internet in 1976?
https://www.garlic.com/~lynn/2009n.html#32 Status of Arpanet/Internet in 1976?
https://www.garlic.com/~lynn/2009n.html#33 Status of Arpanet/Internet in 1976?
https://www.garlic.com/~lynn/2009n.html#34 Status of Arpanet/Internet in 1976?
https://www.garlic.com/~lynn/2009n.html#39 Status of Arpanet/Internet in 1976?
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Follow up Newsgroups: comp.protocols.tcp-ip Date: Fri, 25 Sep 2009 23:39:52 -0400rpw3@rpw3.org (Rob Warnock) writes:
One issue is error drops ... and another issue was congestion. Rate based congestion control is a lot more stable than window-based stuff.
earlier we had been doing some stuff with cyclotomics on FEC. One was reed-solomon ecc for normal transmission ... but if there was packet arrive in error (as opposed to dropped packet) ... rather than retransmit the original packet ... transmit the half-rate viterbi (also encoded with reed-solomon ecc).
XTP has minimum of 3-packet exchange for reliable transaction (compared to minimum of 7-packet exchange for TCP).
I've periodically proposed a non-PKI (certificate-less) XTP SSL
transaction using DNSSEC. Piggy-back (dnssec) registered public key in
the ip-address lookup response. Client then generates random SSL
symmetric key, encodes the XTP packet with the symmetric key and encodes
the symmetric key with the (server's) public key (from the dns
response). some related posts
https://www.garlic.com/~lynn/subpubkey.html#catch22
XTP SSL transaction could then be less expensive than equivalent transaction using vanilla HTTP (w/o encryption).
... bits & pieces from long ago and far away (I've got some amount of the stuff still in boxes someplace):
Protocol Engines 1990 Document Register (revision date 12/14/90) 90-1 SGI Plans XTP Chip - Digital Review 90-2 LAN Protocol Pushed - CS News 90-3 XTP Short Tutorial - Weaver 90-4 XTP/PE Design Considerations - Chesson 90-5 Multicast Strategies for XTP - Weaver 90-6 Extract of Proceedings of Gigabit Workshop - NRI 90-7 VMEbus Controller Implementations Survey - Warnock 90-8 Engineering Report - Gronski 90-9 XTP Workshop Report - Chesson 90-10 Preliminary XBUS and CBUS Specification - Warnock 90-11 Xpress Transfer Protocol Report - Weaver 90-12 N-Party Operation Taxonomy I - Chesson 90-13 ANSI Plan A, B, Straw Vote 90-14 IEEE 802.6 Report - Mollenaur 90-15 Medical Imaging and HS Protocols - Chimiak 90-16 KRM Status - Jan 24, 1990 - Chesson 90-17 NSWC Report - Marlow 90-18 SAFENET Status Report- Cohn 90-19 Minutes of January TAB Meeting - Green 90-20 Requirements for LANS and MANS - ECMA 90-21 PRM Preliminary Interface Specification - Warnock (obsoleted by 90-29) 90-22 January-February Press Clippings 90-23 Paradigm Shift Draft Rev 0 - Moulton (obsoleted by 90-44) 90-24 UVA XTP Status Report - Weaver 90-25 HSP Requirements - X3S3.3 90-26 Soderblom Patient - Chesson 90-27 HSP Requirements - Marlow 90-28 HSP Report - Green 90-29 PRM Preliminary Interface Spec - Warnock 90-30 IEEE 802 Report - Green 90-31 Minutes of X3S3.3 Meeting - Feb. 1990 - Green 90-32 XTP Porting Reference Model - Warnock ... 90-200 KRM Distribution Guide 12/14/90 - Whaley... snip ...
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Opinions on the 'Unix Haters' Handbook'. Newsgroups: alt.folklore.computers Date: Sat, 26 Sep 2009 00:11:15 -0400Charles Richmond <frizzle@tx.rr.com> writes:
... it is almost like some of the stereotype stories about teenagers getting so involved in violent roll-playing games ... they no longer can differentiate fantasy from reality; it is purely the thrill of the game.
the mortgage originators didn't care, they wrote the mortgages as fast as possible w/o regard to risk ... only issue was how much and how fast ... and they took their percentage ... and unloaded them to be somebody else's problem.
... I recently got notified that this was ranked as "best" answer to
(linkedin) question from nearly year ago (there is close parallel to the
unregulated mortgage originators being able to unload everything they
could write w/o regarding to quality ... taking down the economy ... and
the '20s brokers' loans fueling the stock market speculation and crash
of '29):
My Question: How is Subprime crisis impacting other Industries?
Your Answer:
Unregulated mortgage originators found a large untapped source of funds
by packaging mortgages as triple-A rated toxic CDOs. Since they could
unload ever mortgage they could write w/o regard to quality (as triple-A
rated toxic CDOs) ... the question is what kind of mortgages had little
activity. In the past, there was limited source of funds for writing
low-quality mortgages. With triple-A rated toxic CDOs, funds for this
market became almost unlimited. This nearly unlimited source of funds
became very attractive for speculators; no-documentation,
no-downpayment, 1percent, interest only ARMs could be leveraged for
2000% or better ROI (planning on flipping the property before the rate
reset).
Subprime had originally been targeted at 1st time, low-income home
buyers. However, speculators could leverage "sub-prime" all across the
home-owner market. The speculation, in addition to greatly inflating
home prices, made it appear like demand was much larger that it actually
was. As a result, construction companies took out loans to build large
number of additional houses & stripmalls for the apparent big upswing in
demand (anticipating they would sell the houses & stripmalls and pay off
the loans). Companies that supplied material for building, took out
loans to stock the additional supplies. Cities & towns sold bonds to
build all the infrastructure services for all the new housing projects
(anticipating all the additional real estate taxes when the properties
sold ... would fund the bonds).
When the speculation bubble burst, the properties went unsold
... hitting all the construction companies (and their loans), the
building material supply companies (& their loans), and the
municipalities (and their bonds). Bursting of the speculation bubble
then starts to spread throughout much of the economy.
CDOs were used two decades ago during S&L crisis to obfuscate underlying
value and sell for more than they were worth.
Congressional hearings a couple weeks ago looked at toxic CDOs getting
triple-A ratings. Testimony was that both mortgage originators and
rating agencies knew that the toxic CDOs weren't worth triple-A rating
... but the mortgage originators were paying for the triple-A
ratings. This enormously increase the market for these instruments (and
the source of funds)
On the institution side buying all these triple-A rated toxic CDOs
... there was questionable behavior ... they were playing both 1)
long/short mismatch ... which has been known for centuries to take down
institutions and 2) capital leveraged 40-80 times buying triple-A rated
toxic CDOs.
All of the individual characteristics had been around before the
triple-A ratings ... but the availability of funds was severely
limited. Getting the triple-A ratings on toxic CDOs contributed to all
the isolated hotbeds of greed and corruption to turn into a firestorm.
Links:
http://www.forbes.com/2007/11/13/citigroup-suntrust-siv-ent-fin-cx_bh_1113hamiltonmatch.html
... snip ...
re:
https://www.garlic.com/~lynn/2008q.html#20 How is Subprime crisis impacting other Industries?
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Microprocessors with Definable MIcrocode Newsgroups: alt.folklore.computers Date: Sat, 26 Sep 2009 00:45:02 -0400Charles Richmond <frizzle@tx.rr.com> writes:
above references that 29k was "descended from the berkeley risc design (and the ibm 801 project)".
one of the big efforts for 801 in the late 70s and early 80s was to replace the large number of internal microprocessors that then were microcoded for low-end & mid-range 370s ... as well as large number of embedded processors in various products & controllers (as well as going to be the original processor for AS/400).
that 801/Iliad effort eventually floundered ... as/400 quickly doing a
cisc, 4331/4341 follow-ons (4361 & 4381) doing cisc, and
microprocessors continued business as usual for a time. With the
floundering of those projects, some number of 801 engineers left and
showed up at other companies. I have some vague recollection that one
showd up at AMD working on 29K ... and there was some legal wrangling
for a time about possible 801/Iliad secrets leaking. misc. past 801,
risc, iliad, romp, rios, power/pc, etc posts
https://www.garlic.com/~lynn/subtopic.html#801
The other thing was some number of the silicon valley chips shop in the 70s and early 80s (before the availability of engineering workstations) were large vm370 shops (some even cp67 before that) ... and some of their support people would show up at monthly virtual machine user group meetings held at SLAC. I remember getting amd 2900 and early amd 29k books from such a contact.
the cpushack reference mentions that AMD discontinued the 29k in 1985, but because of its mission critical uses, they sold it off to Honeywell ... where it is still being used today: Boeing 777 - All Models, Boeing 737-600/700/800, Boeing 717, Federal Express MD-80s, US Airforce KC-10, US Airforce C5B Galaxy
a little more drift on 29050:
Versatile Integrated Avionics (VIA)
http://www.honeywell.com/sites/aero/Military-Aircraft3_C5470C98A-2B24-D58B-E116-A12EE0618C23_HE5F5AEBE-E7E3-B706-E36D-4D58219C52D0.htm
Boeing Flies on 99% Ada
http://www.adaic.org/atwork/boeing.html
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Opinions on the 'Unix Haters' Handbook'. Newsgroups: alt.folklore.computers Date: Sat, 26 Sep 2009 00:55:26 -0400Walter Bushell <proto@panix.com> writes:
the other scenario was that everything was fiddled to do what the traders & deal people wanted to do ... risk managers were overruled and/or told to adjust the parameters until they supported what the traders & deal people wanted.
example was article from 18Sept2008
How Wall Street Lied to Its Computers
http://bits.blogs.nytimes.com/2008/09/18/how-wall-streets-quants-lied-to-their-computers/
article from summer 2007:
Subprime = Triple-A ratings? or 'How to Lie with Statistics' (gone 404 but lives on at the wayback machine)
https://web.archive.org/web/20071111031315/http://www.bloggingstocks.com/2007/07/25/subprime-triple-a-ratings-or-how-to-lie-with-statistics/
misc. past posts mentioning above articles:
https://www.garlic.com/~lynn/2008n.html#49 VMware Chief Says the OS Is History
https://www.garlic.com/~lynn/2008n.html#52 Technology and the current crisis
https://www.garlic.com/~lynn/2008n.html#53 Your thoughts on the following comprehensive bailout plan please
https://www.garlic.com/~lynn/2008n.html#56 VMware Chief Says the OS Is History
https://www.garlic.com/~lynn/2008n.html#65 Whether, in our financial crisis, the prize for being the biggest liar is
https://www.garlic.com/~lynn/2008n.html#69 Another quiet week in finance
https://www.garlic.com/~lynn/2008n.html#72 Why was Sarbanes-Oxley not good enough to sent alarms to the regulators about the situation arising today?
https://www.garlic.com/~lynn/2008n.html#78 Isn't it the Federal Reserve role to oversee the banking system??
https://www.garlic.com/~lynn/2008n.html#80 Why did Sox not prevent this financal crisis?
https://www.garlic.com/~lynn/2008n.html#82 Fraud in financial institution
https://www.garlic.com/~lynn/2008o.html#15 Financial Crisis - the result of uncontrolled Innovation?
https://www.garlic.com/~lynn/2008o.html#18 Once the dust settles, do you think Milton Friedman's economic theories will be laid to rest
https://www.garlic.com/~lynn/2008o.html#19 What's your view of current global financial / economical situation?
https://www.garlic.com/~lynn/2008o.html#26 SOX (Sarbanes-Oxley Act), is this really followed and worthful considering current Financial Crisis?
https://www.garlic.com/~lynn/2008o.html#28 Does anyone get the idea that those responsible for containing this finanical crisis are doing too much?
https://www.garlic.com/~lynn/2008o.html#34 The human plague
https://www.garlic.com/~lynn/2008o.html#75 In light of the recent financial crisis, did Sarbanes-Oxley fail to work?
https://www.garlic.com/~lynn/2008o.html#82 Greenspan testimony and securization
https://www.garlic.com/~lynn/2008o.html#83 Chip-and-pin card reader supply-chain subversion 'has netted millions from British shoppers'
https://www.garlic.com/~lynn/2008p.html#8 Global Melt Down
https://www.garlic.com/~lynn/2008p.html#70 Is there any technology that we are severely lacking in the Financial industry?
https://www.garlic.com/~lynn/2008q.html#49 Have not the following principles been practically disproven, once and for all, by the current global financial meltdown?
https://www.garlic.com/~lynn/2008q.html#50 Obama, ACORN, subprimes (Re: Spiders)
https://www.garlic.com/~lynn/2008r.html#58 Blinkenlights
https://www.garlic.com/~lynn/2008r.html#64 Is This a Different Kind of Financial Crisis?
https://www.garlic.com/~lynn/2008s.html#8 Top financial firms of US are eyeing on bailout. It implies to me that their "Risk Management Department's" assessment was way below expectations
https://www.garlic.com/~lynn/2008s.html#9 Blind-sided, again. Why?
https://www.garlic.com/~lynn/2008s.html#23 Garbage in, garbage out trampled by Moore's law
https://www.garlic.com/~lynn/2008s.html#29 Let IT run the company!
https://www.garlic.com/~lynn/2008s.html#35 Is American capitalism and greed to blame for our financial troubles in the US?
https://www.garlic.com/~lynn/2008s.html#55 Is this the story behind the crunchy credit stuff?
https://www.garlic.com/~lynn/2008s.html#62 Garbage in, garbage out trampled by Moore's law
https://www.garlic.com/~lynn/2009.html#14 What are the challenges in risk analytics post financial crisis?
https://www.garlic.com/~lynn/2009.html#63 CROOKS and NANNIES: what would Boyd do?
https://www.garlic.com/~lynn/2009.html#80 Are reckless risks a natural fallout of "excessive" executive compensation ?
https://www.garlic.com/~lynn/2009b.html#36 A great article was posted in another BI group: "To H*** with Business Intelligence: 40 Percent of Execs Trust Gut"
https://www.garlic.com/~lynn/2009b.html#53 Credit & Risk Management ... go Simple ?
https://www.garlic.com/~lynn/2009b.html#54 In your opinion, which facts caused the global crise situation?
https://www.garlic.com/~lynn/2009b.html#65 What can agencies such as the SEC do to insure us that something like Madoff's Ponzi scheme will never happen again?
https://www.garlic.com/~lynn/2009c.html#4 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#28 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009d.html#16 The Formula That Killed Wall Street
https://www.garlic.com/~lynn/2009d.html#18 HSBC is expected to announce a profit, which is good, what did they do differently?
https://www.garlic.com/~lynn/2009d.html#30 I need insight on the Stock Market
https://www.garlic.com/~lynn/2009d.html#36 Bernanke Says Regulators Must Protect Against Systemic Risks
https://www.garlic.com/~lynn/2009d.html#40 Bernanke Says Regulators Must Protect Against Systemic Risks
https://www.garlic.com/~lynn/2009d.html#59 Quiz: Evaluate your level of Spreadsheet risk
https://www.garlic.com/~lynn/2009e.html#8 The background reasons of Credit Crunch
https://www.garlic.com/~lynn/2009g.html#1 Future of Financial Mathematics?
https://www.garlic.com/~lynn/2009g.html#31 OODA-loop obfuscation
https://www.garlic.com/~lynn/2009h.html#29 Analysing risk, especially credit risk in Banks, which was a major reason for the current crisis
https://www.garlic.com/~lynn/2009j.html#38 what is mortgage-backed securities?
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Sat, 26 Sep 2009 10:08:09 -0400jmfbahciv <jmfbahciv@aol> writes:
... centralized physically, computationally, and as significant administratively. however, the arpanet scenario about saturating bandwidth was all the IMPs exchanging lots of activity & status information and then having all the IMPs coming to decisions based attempting to have all information distributed to all IMPs.
... note that in the tymnet reference ... they mention having
significantly more efficient infrastructure
https://www.garlic.com/~lynn/2009n.html#27 Continous Systems Modelling Package
https://www.garlic.com/~lynn/2009n.html#28 Status of Arpanet/Internet in 1976?
https://www.garlic.com/~lynn/2009n.html#45 Status of Arpanet/Internet in 1976?
the internal network didn't have the "control" characterisitic ... misc.
past posts mentioning internal network & being larger than the
arpanet/internet from just about the beginning until sometime late '85
or possibly early '86
https://www.garlic.com/~lynn/subnetwork.html#internalnet
there is folklore story about somebody from corporate hdqtrs discovering the internal network circa 1980 and doing an investigation. at one point the person explains that there has been detailed study of what would be required to implement a fully distributed operation ... and the resources involved. supposedly the people-yrs to implement the supposed "distribtued operation" of the internal network is so humongous, that it would have had to show up as an individual budget line-item at the corporate level ... and no such line-item has ever should up (well beyond the capability of a single person at the cambridge science center).
I had gotten blamed for computer conferencing on the internal network in the late 70s and early 80s ... and I don't remember whether the above incident predated corporate becoming aware of the online computer conferencing characteristic.
for more drift, on-going thread in comp.protocols.tcp-ip
https://www.garlic.com/~lynn/2009n.html#41
https://www.garlic.com/~lynn/2009n.html#44
including mention of Greg Chesson inventing XTP (for a couple yrs, I was
on the XTP technical advisery board)
https://www.garlic.com/~lynn/2009n.html#46
taking HSP to x3s3.3 ... mentioned earlier in this thread
https://www.garlic.com/~lynn/2009n.html#33 Status of Arpanet/Internet in 1976?
was done out of XTP effort ... the most recent post in the comp.protocols.tcp-ip includes part of the XTP TAB document register ... which has references to x3s3.3 activity (some of the TAB documents I have partial softcopy ... majority is in boxes someplace).
minor reference to Greg having earlier done UUCP
http://www.uucp.org/papers/chesson.html
past posts mentionin xtp &/or hsp (and/or OSI & x3s3.3):
https://www.garlic.com/~lynn/subnetwork.html#xtphsp
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Follow up Newsgroups: comp.protocols.tcp-ip Date: Sat, 26 Sep 2009 13:17:31 -0400bits & pieces from (20yrs ago):
the above multicast article reference has mention of VMTP which has IETF RFC1045.
for some more drift ... my rfc index
https://www.garlic.com/~lynn/rfcietff.htm
re:
https://www.garlic.com/~lynn/2009n.html#41 Follow up
https://www.garlic.com/~lynn/2009n.html#44 Follow up
https://www.garlic.com/~lynn/2009n.html#46 Follow up
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Security Newsgroups: alt.computer.security Date: Sun, 27 Sep 2009 10:22:53 -0400Randy Yates <yates@ieee.org> writes:
the problem was that the science center cp67 time-sharing service also had numerous (non-employee) users (students and others) from various educational institutions (harvard, mit, bu, etc) in the boston/cambridge area. as a result, there was lots of security concerns that the effort would leak (confidential) information about unannounced products.
so the decision was made that the modifications (for 370 virtual machines) were made to version of cp67 system that ran in a 360/67 virtual machine (kept isolated from what the non-employees had access to).
then a different cp67 was modified to run on 370 machine (using the new instructions and building the 370 virtual memory tables ... rather than the 360 virtual memory tables). the result was:
360/67 hardware -> cp/67 running on real 360/67 providing 360 virtual machines -> cp/67 running in 360 virtual machine providing 370 virtual machines -> cp/67 running in 370 virtual machine providing 370 virtual machine -> cms running in 370 virtual machineall of this was operational and in regular use a year before there was engineering 370s with virtual memory hardware support (circa 1970) ... and while non-employees also had online access to the same, underlying (unmodified) cp67 virtual machine system (running on the real 360/67 hardware).
"real" virtual machine implementations are recursive.
there was an incident where information about 370 virtual memory was leaked ... but it didn't involve the above effort. an internal confidential document was copied and made it into the hands of somebody from the press. there was an investigation attempting to identify who leaked the information. one of the results were that all the corporate copier machines were modified so that they left (unique) identifiable mark on paper copies (indicating which machine made the copy).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: lynn@GARLIC.COM (Anne & Lynn Wheeler) Subject: Re: Long parms...again Newsgroups: bit.listserv.ibm-main Date: 27 Sep 2009 08:11:04 -0700wmhblair@COMCAST.NET (William H. Blair) writes:
in any case there was an internal computer conference (CENTURY) discussing the
upcoming y2k problem ... old post in the discussion from somebody
working with nasa about some related problems:
Date: 7 December 1984, 14:35:02 CST
To: Distribution
1.In 1969, Continental Airlines was the first (insisted on being the
first) customer to install PARS. Rushed things a bit, or so I hear. On
February 29, 1972, ALL of the PARS systems canceled certain
reservations automatically, but unintentionally. There were (and still
are) creatures called "coverage programmers" who deal with such
situations.
2.A bit of "cute" code I saw once operated on a year by loading a
byte of packed data into a register (using INSERT CHAR), then used LA
R,1(R) to bump the year. Got into a bit of trouble when the year 196A
followed 1969. I guess the problem is not everyone is aware of the odd
math in calendars. People even set up new religions when they discover
new calendars (sometimes).
3.We have an interesting calendar problem in Houston. The Shuttle
Orbiter carries a box called an MTU (Master Timing Unit). The MTU gives
yyyyddd for the date. That's ok, but it runs out to ddd=400 before it
rolls over. Mainly to keep the ongoing orbit calculations smooth. Our
simulator (hardware part) handles a date out to ddd=999. Our simulator
(software part) handles a date out to ddd=399. What we need to do, I
guess, is not ever have any 5-week long missions that start on New
Year's Eve. I wrote a requirements change once to try to straighten
this out, but chickened out when I started getting odd looks and
snickers (and enormous cost estimates).
... snip ... top of post, old email index
past threads, posting the above:
https://www.garlic.com/~lynn/99.html#24 BA Solves Y2K (Was: Re: Chinese Solve Y2K)
https://www.garlic.com/~lynn/2000.html#94 Those who do not learn from history...
https://www.garlic.com/~lynn/2003p.html#21 Sun researchers: Computers do bad math ;)
https://www.garlic.com/~lynn/2006r.html#16 Was FORTRAN buggy?
past posts mentioning the internal network
https://www.garlic.com/~lynn/subnetwork.html#internet
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Follow up Newsgroups: comp.protocols.tcp-ip Date: Sun, 27 Sep 2009 13:51:04 -0400rpw3@rpw3.org (Rob Warnock) writes:
as a result there was effort to take xtp(hsp) to x3s3.3 (ISO chartered US standards group responsible for level 3&4 in the OSI model) for standardization. However x3s3.3 was under ISO (charter) restrictions to not do standardization for stuff that violated the OSI model ... and there were various pieces of XTP/HSP that violated the OSI model (which then precluded x3s3.3 ever really doing anything with xtp/hsp).
on the tcp/internet side ... there were lots of stuff with wide-spread (widely deployed) commodity implementations and XTP was moving up the value chain ... which represented some barrier on the internet side.
tcp/ip was the technology basis for the modern internet ... but the nsfnet backbone was the operational basis for the modern internet (and CIX was going to be the business basis for the modern internet).
we had been involved in some of the early NSFNET backbone activity as well as doing our own highspeed backbone (copper, fiber, satellite, T1 & higher speed). when the T1 NSFNET backbone RFP was released, internal politics prevented us from bidding. The director of NSF wrote a letter to the corporation (co-signed by some others), copying the CEO and referenced wanting us involved and things like what we already had running was at least five years ahead (possibly 20) of all RFP responses to build something new. That just made the internal politics worse.
re:
https://www.garlic.com/~lynn/2009n.html#41 Follow up
https://www.garlic.com/~lynn/2009n.html#44 Follow up
https://www.garlic.com/~lynn/2009n.html#46 Follow up
https://www.garlic.com/~lynn/2009n.html#51 Follow up
misc. past posts mentioning nsfnet backbone
https://www.garlic.com/~lynn/subnetwork.html#nsfnet
misc. past posts mentiong HSDT (high-speed data transport) project
https://www.garlic.com/~lynn/subnetwork.html#hsdt
misc. past posts mentioning internal network
https://www.garlic.com/~lynn/subnetwork.html#internalnet
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Hexadecimal Kid - articles from Computerworld wanted Newsgroups: alt.folklore.computers Date: Sun, 27 Sep 2009 23:10:59 -0400Charles Richmond <frizzle@tx.rr.com> writes:
misc. past posts
https://www.garlic.com/~lynn/2006f.html#41 The Pankian Metaphor
https://www.garlic.com/~lynn/2006f.html#44 The Pankian Metaphor
https://www.garlic.com/~lynn/2006g.html#9 The Pankian Metaphor
https://www.garlic.com/~lynn/2006g.html#14 The Pankian Metaphor
https://www.garlic.com/~lynn/2006g.html#27 The Pankian Metaphor
https://www.garlic.com/~lynn/2006h.html#2 The Pankian Metaphor
https://www.garlic.com/~lynn/2006h.html#3 The Pankian Metaphor
https://www.garlic.com/~lynn/2006h.html#4 The Pankian Metaphor
https://www.garlic.com/~lynn/2006h.html#17 The Pankian Metaphor
https://www.garlic.com/~lynn/2006h.html#19 The Pankian Metaphor
https://www.garlic.com/~lynn/2006h.html#33 The Pankian Metaphor
https://www.garlic.com/~lynn/2006o.html#61 Health Care
https://www.garlic.com/~lynn/2006p.html#17 Health Care
https://www.garlic.com/~lynn/2006r.html#0 Cray-1 Anniversary Event - September 21st
https://www.garlic.com/~lynn/2006t.html#26 Universal constants
https://www.garlic.com/~lynn/2007j.html#20 IBM Unionization
https://www.garlic.com/~lynn/2007j.html#91 IBM Unionization
https://www.garlic.com/~lynn/2007k.html#19 Another "migration" from the mainframe
https://www.garlic.com/~lynn/2007o.html#74 Horrid thought about Politics, President Bush, and Democrats
https://www.garlic.com/~lynn/2007p.html#22 U.S. Cedes Top Spot in Global IT Competitiveness
https://www.garlic.com/~lynn/2007q.html#7 what does xp do when system is copying
https://www.garlic.com/~lynn/2007s.html#1 Translation of IBM Basic Assembler to C?
https://www.garlic.com/~lynn/2007t.html#13 Newsweek article--baby boomers and computers
https://www.garlic.com/~lynn/2007t.html#14 Newsweek article--baby boomers and computers
https://www.garlic.com/~lynn/2007t.html#15 Newsweek article--baby boomers and computers
https://www.garlic.com/~lynn/2007t.html#24 Translation of IBM Basic Assembler to C?
https://www.garlic.com/~lynn/2007t.html#25 Newsweek article--baby boomers and computers
https://www.garlic.com/~lynn/2007t.html#33 Newsweek article--baby boomers and computers
https://www.garlic.com/~lynn/2007t.html#35 Newsweek article--baby boomers and computers
https://www.garlic.com/~lynn/2007v.html#26 2007 Year in Review on Mainframes - Interesting
https://www.garlic.com/~lynn/2008.html#57 Computer Science Education: Where Are the Software Engineers of Tomorrow?
https://www.garlic.com/~lynn/2008d.html#40 Computer Science Education: Where Are the Software Engineers of Tomorrow?
https://www.garlic.com/~lynn/2008e.html#50 fraying infrastructure
https://www.garlic.com/~lynn/2008f.html#86 Banks failing to manage IT risk - study
https://www.garlic.com/~lynn/2008g.html#1 The Workplace War for Age and Talent
https://www.garlic.com/~lynn/2008h.html#3 America's Prophet of Fiscal Doom
https://www.garlic.com/~lynn/2008h.html#26 The Return of Ada
https://www.garlic.com/~lynn/2008i.html#98 dollar coins
https://www.garlic.com/~lynn/2008n.html#8 Taxcuts
https://www.garlic.com/~lynn/2008n.html#9 Taxcuts
https://www.garlic.com/~lynn/2008n.html#17 Michigan industry
https://www.garlic.com/~lynn/2009f.html#20 What is the real basis for business mess we are facing today?
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Opinions on the 'Unix Haters' Handbook'. Newsgroups: alt.folklore.computers Date: Mon, 28 Sep 2009 00:21:23 -0400Peter Flass <Peter_Flass@Yahoo.com> writes:
all the stuff went on for some time ... including the adjustable rate mortgages ... the issue was that there wasn't much money available in the market for the practices to do much harm.
major items fueling the current situation were
GLBA (Gramm-Leach-Bliley, "bank modernization act", repeal of Glass-Steagall) allowing regulated financial institutions to have unregulated investment banking arms (which then put the regulated financial institution at enormous risk as a result of their unregulated activity and various things being carried off balanace)
and
Commodity futures modernization act (again with Gramm) exempted over-the-counter direvatives (like credit default swaps) from regulation (which took down AIG).
25 People to Blame for the Financial Crisis - Phil Gramm
http://content.time.com/time/specials/packages/article/0,28804,1877351_1877350_1877330,00.html
Enron and Gramm's wife was also involved in some of this ... recent
post with several article references:
https://www.garlic.com/~lynn/2009i.html#60 In the USA "financial regulator seeks power to curb excess speculation."
unregulated mortgage originators could get enormous funding (trillions) for all the sub-prime loans by packaging them up as toxic CDOs, buying triple-A ratings for the toxic CDOs and selling them to the world.
They managed to do large trillions (low-income market is only small percentage) in this way. Being able to sell off the loans as fast as possible, eliminated any motivation to care about loan quality and borrowers qualifications
In earlier times, mortgages were done by regulated financial institution using deposits as source of funds. With GLBA & repeal of Glass-Steagall, regulated financial institutions could use their unregulated investment banking arms to move the banks assets (buying triple-A rated toxic CDOs, which was in turn providing the enormous funds for unregulated, non-depository mortgage originators to write mortgages with the only qualification being how much and how fast).
however speculators found no-documentation, no-downpayment, interest-only, 1% ARMs extremely attactive ... since the carrying cost was significantly less than real-estate inflation in many parts of the country (possibly as high as 2000% ROI ... and they tended to buy huge amount of stuff way out of the low-income category ... like jumbo loans for large McMansions).
Again with large trillions in funding (in large part indirectly from regulated financial institutions) being poured into the unregulated mortgage origiantors (in circuitous manner, skirting regulations) ... enabling vast numbers/amounts of mortgages being written as sub-prime (for speculators); far beyond any kind of "low-income" designation ... that resulted in the huge damage to the economy.
25 People to Blame for the Financial Crisis - Angelo Mozilo
http://content.time.com/time/specials/packages/article/0,28804,1877351_1877350_1877339,00.html
from above:
Countrywide wasn't the first to offer exotic mortgages to borrowers with
a questionable ability to repay them. In its all-out embrace of such
sales, however, it did legitimize the notion that practically any adult
could handle a big fat mortgage.
... snip ...
unregulated, non-depository loan originators no longer needed to care anything at all about borrower qualifications ... their bottom line was purely how many loans they could write and how fast ... since being able to unload them all as triple-A rated, toxic CDOs ... they no longer carried any risk and had no reason to care. If an "adult" wasn't handy ... they could always write a half-dozen mortgages to a speculator (they no longer had any reason to care).
I've commented before that the hot beds of greed and corruption have always been there ... but it was being able to buy triple-A ratings for the toxic CDOs and the repeal of Glass-Steagall ... that enabled the individual hot beds of greed and corruption to turn into an economic firestorm and the current economic nightmare (i.e. allowing what would have been possibly a tens of billions problem to turn into a tens of trillions problem ... a thousand-fold increase in the magnitude of the problem).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Evolution of Floating Point Newsgroups: alt.folklore.computers Date: Mon, 28 Sep 2009 00:28:04 -0400Walter Bushell <proto@panix.com> writes:
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Opinions on the 'Unix Haters' Handbook'. Newsgroups: alt.folklore.computers Date: Mon, 28 Sep 2009 10:38:53 -0400Anne & Lynn Wheeler <lynn@garlic.com> writes:
aka ... if it had been sub-prime to low-income by regulated, depository financial institutions... it wouldn't even have been a blip on the screen ... it was trillions in uncontrolled, unregulated (by unregulated mortgage originators not subject to such requirements) sub-prime to everybody else ... including huge amounts to speculators ... that resulted in the economic firestorm
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Evolution of Floating Point Newsgroups: alt.folklore.computers Date: Mon, 28 Sep 2009 11:35:45 -0400Charles Richmond <frizzle@tx.rr.com> writes:
155 was faster than 145 ... even tho 145 had approx. 400+nsec memory (compared to 155 2mic memory) because 155 had cache (8kbytes; as long as what you were doing fit within the small 155 cache size). the size of many of today's programs wouldn't even fit in 155 real storage (independent of the data).
announcement that virtual memory could be retrofit with (purchased) hardware upgrade ... came about the same time as 370/158 ... which had approx. same speed memory as 145 (and cache).
the gigabyte refrigerators+ size were a decade after 155.
155 announced 30jun70, withdrawn 23dec77
http://www-03.ibm.com/ibm/history/exhibits/mainframe/mainframe_PP3155.html
above shown with 2314 string (9th drive was "spare" could be used for service and/or staging mounting packs).
158 announced 2aug72 and withdrawn 15sep80
http://www-03.ibm.com/ibm/history/exhibits/mainframe/mainframe_PP3158.html
shown with 8-drive 3330 string
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Hexadecimal Kid - articles from Computerworld wanted Newsgroups: alt.folklore.computers Date: Mon, 28 Sep 2009 12:10:10 -0400Dave Garland <dave.garland@wizinfo.com> writes:
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Evolution of Floating Point Newsgroups: alt.folklore.computers Date: Mon, 28 Sep 2009 19:17:47 -0400Peter Flass <Peter_Flass@Yahoo.com> writes:
one of the big hacks for initial prototype of SVS was to wire CP67's CCWTRANS into the side of MVT input/output supervisor (EXCP processing).
base OS/360 environment had applications (and/or libraries running in application space) building i/o channel programs in the application space ... and then doing a supervisor call EXCP ... to execute the passed channel program.
MVT running in virtual machine ... or VS2 (whether SVS or MVS) is passed pointer to channel program filled with virtual addresses. A "shadow" copy of the channel program has to be built that substitutes the real address (for the virtual addresses) before being able to execute the (shadow) channel program (as opposed to the "passed" channel program). The initial pass for VS2 borrowed CCWTRANS from CP67 that would scan the passed channel program ... building a shadow duplicate, substituting real addresses for the virtual addresses (as well as fetching and pinning the required virtual pages in real memory).
In theory, the migration from SVS (single address space) to MVS (multiple address space) gave each application its own 16mbyte virtual address space. However, os/360 is a pointer passing intensive paradigm ... so each virtual address space was populated with 8mbyte kernel image (taking half of each 16mbyte virtual address space).
In MVT and SVS there were also these "sub-system" applications that sat outside the kernel ... but were extensively used by applications (using pointer passing paradigm). Migration to MVS moved each of these sub-system applications into their own virtual address space. The problem sub-system problem was having normal application make a sub-system call, passing a pointer ... the call passing thru the kernel ... with the kernel switching to the sub-system address space. The sub-system is now got a pointer to a parameter list back in the original application address space.
Solution was something called a "common segment" ... initially a one megabyte area that existed in every address space ... where application could stuff parameter values ... and then make a subsystem call passing a parameter to the address of the parameter list in the common segment.
For larger systems, "common segment" grew to be 4-5 mbytes ... which for many installations left only 3mbytes (and shrinking) for application actual execution/use.
Burlington chip house was having problems with fortran chip programs that were just hanging in at 7mbytes max ... on specially configured MVS system trimmed to be no larger than 9mbytes. Minor changes to the fortran program would exceed 7mbytes or minor changes to mvs would have it exceed 9mbytes ... in either case, program would no longer be able to execute.
Some things were done for burlington to allow their programs to run with
vm370/cms ... giving the program nearly all of a 16mbyte virtual address
space. some past references:
https://www.garlic.com/~lynn/2006b.html#39 another blast from the past
https://www.garlic.com/~lynn/2006c.html#0 Multiple address spaces
https://www.garlic.com/~lynn/2007g.html#59 IBM to the PCM market(the sky is falling!!!the sky is falling!!)
https://www.garlic.com/~lynn/2007g.html#82 IBM to the PCM market
https://www.garlic.com/~lynn/2008r.html#32 What if the computers went back to the '70s too?
old email mentioning the issue:
https://www.garlic.com/~lynn/2006b.html#email800310
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Opinions on the 'Unix Haters' Handbook'. Newsgroups: alt.folklore.computers Date: Mon, 28 Sep 2009 19:58:15 -0400Walter Bushell <proto@panix.com> writes:
regulated, depository financial institutions weren't making the loans.
unregulated, non-depository mortgage originators were making the loans. in the past, unregulated, non-depository mortgage originators were quite limited (in the amount of loans) because of limited available of funds to the institutions (not like regulated depository financial institutions that had deposits to use).
the big change came when unregulated, non-depository mortgage originators found that they could package the loans as toxic CDOs and pay the rating agencies to give the toxic CDOs triple-A ratings" ... creating nearly unlimited source of funds for the unregulated, non-depository mortgage originators.
it turns out that some of the large regulated, depository financial institutions were actually providing lots of the funds ... but in a circuitous, round-about unregulated way, where their unregulated investment banking arms (courtesy of GLBA repealing Glass-Steagall) buy the triple-A rated toxic CDOs. The investment banking side of the house would purchase these instruments ... because they could get compensation based on percent of the transaction value ... unrelated to whether the instruments made any money or not. There is some analogy to the old problem with financial advisers "churning accounts" (doing lots of unnecessary stock trades because they earned a percent from each trade, regardless of whether there was profit or loss).
In effect, the same thing was happening at the unregulated, non-depsoitory mortgage originators ... getting a percent of the transaction (size) ... unrelated to whether the transaction was profitable or not (since they immediately unloaded the mortgages as triple-A rated toxic CDOs and no longer had to care about whether the mortgage performed).
Individuals were making huge amounts from the way the transactions were structured ... w/o regard to profitability of the transactions.
Trillions of dollars of these toxic CDOs are now setting (off-the-books) at many of these large (too big to fail) regualted financial institutions. In theory, the original TARP funds justification (to congress ... and for which congress approved the funds for) ... was to buy up these toxic CDOs. However, apparently somebody quickly realized that the amount of TARP funds represented barely a drop in the bottom of the bucket compared to the aggregate magnitude of the toxic CDOs held by various (too big to fail) financial institutions. So instead ... TARP funds were divereted to temporarily prop up these (too big to fail) financial institutions, while they tried to figure out what to do about the real problem (the large trillions in mortgage backed toxic CDOs).
In theory, if these financial instruments (mortgage backed toxic CDOs) were to be brought back onto the books (or if they had been there all along), these (too big to fail) financial institutions would have to be declared insolvent and liquidated.
there was some effort trying to figure out from the annual reports of
the four largest (too big to fail) regulated financial institutions
... guessing that those four held possibly $5.2 trillion in
(off-the-books) toxic CDOs. misc. past posts mentiong "Bank's Hidden
Junk Menaces $1 Trillion Purge"
https://www.garlic.com/~lynn/2009e.html#23 Should FDIC or the Federal Reserve Bank have the authority to shut down and take over non-bank financial institutions like AIG?
https://www.garlic.com/~lynn/2009e.html#36 Architectural Diversity
https://www.garlic.com/~lynn/2009e.html#53 Are the "brightest minds in finance" finally onto something?
https://www.garlic.com/~lynn/2009e.html#70 When did "client server" become part of the language?
https://www.garlic.com/~lynn/2009e.html#79 Are the "brightest minds in finance" finally onto something?
https://www.garlic.com/~lynn/2009f.html#27 US banking Changes- TARP Proposl
https://www.garlic.com/~lynn/2009f.html#31 What is the real basis for business mess we are facing today?
https://www.garlic.com/~lynn/2009f.html#35 US banking Changes- TARP Proposl
https://www.garlic.com/~lynn/2009f.html#38 On whom or what would you place the blame for the sub-prime crisis?
https://www.garlic.com/~lynn/2009f.html#47 TARP Disbursements Through April 10th
https://www.garlic.com/~lynn/2009f.html#49 Is the current downturn cyclic or systemic?
https://www.garlic.com/~lynn/2009f.html#53 What every taxpayer should know about what caused the current Financial Crisis
https://www.garlic.com/~lynn/2009g.html#3 Do the current Banking Results in the US hide a grim truth?
https://www.garlic.com/~lynn/2009h.html#79 The $4 trillion housing headache
https://www.garlic.com/~lynn/2009i.html#60 In the USA "financial regulator seeks power to curb excess speculation."
https://www.garlic.com/~lynn/2009i.html#77 Financial Regulatory Reform - elimination of loophole allowing special purpose institutions outside Bank Holding Company (BHC) oversigh
https://www.garlic.com/~lynn/2009j.html#35 what is mortgage-backed securities?
https://www.garlic.com/~lynn/2009j.html#69 64 Cores -- IBM is showing a prototype already
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Evolution of Floating Point Newsgroups: alt.folklore.computers Date: Tue, 29 Sep 2009 19:32:38 -0400ArarghMail909NOSPAM writes:
system convention was to load programs on double-word boundary ... and there were assembler directives for full-word & double-word bounardies (from start of program ... assumed to be on double-word boundary).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: another item related to ASCII vs. EBCDIC Newsgroups: alt.folklore.computers Date: Tue, 29 Sep 2009 20:42:52 -0400"Joe Morris" <j.c.morris@verizon.net> writes:
at one point FSD said they wanted a review of HSDT projects ... some
past posts mentioning HSDT
https://www.garlic.com/~lynn/subnetwork.html#hsdt
I said I'd give an all day presentation ... imagine my surpise when something like 30 people showed up. Later, imagine my astonishment when FSD attempted to bill HSDT for that day for all 30 people.
misc. old boyd stories mentioning pentagon:
https://www.garlic.com/~lynn/2001e.html#82 The Mind of War: John Boyd and American Security
https://www.garlic.com/~lynn/2002o.html#38 META: Newsgroup cliques?
https://www.garlic.com/~lynn/2003h.html#57 employee motivation & executive compensation
https://www.garlic.com/~lynn/2004b.html#13 The BASIC Variations
https://www.garlic.com/~lynn/2004d.html#61 If you're going to bullshit, eschew moderation
https://www.garlic.com/~lynn/2005n.html#14 Why? (Was: US Military Dead during Iraq War
https://www.garlic.com/~lynn/2005t.html#13 Dangerous Hardware
https://www.garlic.com/~lynn/2005t.html#16 Dangerous Hardware
https://www.garlic.com/~lynn/2006f.html#14 The Pankian Metaphor
https://www.garlic.com/~lynn/2006g.html#13 News Release
https://www.garlic.com/~lynn/2006h.html#4 The Pankian Metaphor
https://www.garlic.com/~lynn/2007h.html#69 John W. Backus, 82, Fortran developer, dies
https://www.garlic.com/~lynn/2007h.html#71 John W. Backus, 82, Fortran developer, dies
https://www.garlic.com/~lynn/2007i.html#5 John W. Backus, 82, Fortran developer, dies
https://www.garlic.com/~lynn/2008c.html#52 Current Officers
https://www.garlic.com/~lynn/2009e.html#53 Are the "brightest minds in finance" finally onto something?
https://www.garlic.com/~lynn/2009g.html#16 USAF officers slammed for pranging Predators on manual
https://www.garlic.com/~lynn/2009j.html#42 Mission Control & Air Cooperation -- Part I
https://www.garlic.com/~lynn/2009j.html#65 Infosec As a Form of Asymmetric Warfare
https://www.garlic.com/~lynn/2009m.html#16 comp.arch has made itself a sitting duck for spam
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Evolution of Floating Point Newsgroups: alt.folklore.computers Date: Tue, 29 Sep 2009 21:06:42 -0400ArarghMail909NOSPAM writes:
linker/loaded combining object sizes ... always started next program/object on double word boundary. object may not be multiple of double words ... but next object/program would always be on the next double world boundary ... even if the previous object was not multiple of double word.
assembler had statements like
ds 0h ... align on half-word boundary
ds 0f ... align on full-word boundary
ds 0d ... align on double word boundary
... predicated on object/program always starting on double word
boundary. also
cnop 0,4example from:
CNOP 0,4
BAL 13,START
DC 20A(0)
START ST 13,8(11)
CNOP would conditional insert "NOP" instructions (possible four byte
conditional branch with zero condition and/or two byte conditional
branch register with zero condition). The above makes sure that four
byte "BAL 13,START" starts on full-word boundary ... so the following
address is also on full-word boundary. the following "DC 20A(0)"
allocates 20 4-byte, full-word aligned words.
The BAL stores the "nominal" return address ... which is actually the start of a 80 byte (save) area ... and branches around the storage (never intending to use the value in 13 as a "return" address ... but as the address of the storage area). The above operation wouldn't be correct if the "BAL 13,START" was only half-word aligned (as opposed to full-word aligned) ... since the address in 13 wouldn't then be full-word aligned address.
assembler generation of instructions is predicated on programs & objects being at least half-word align ... in order to make sure that instructions occur on at least half-word boundaries. "dc 0d" & "cnop 0,8" ... for double-word boundary ... is predicated on programs & objects being at least double-word aligned.
Newer directives were introduced for later gernations of link/loaders ... that would allow forcing program/object to 4k boundary.
I originally used such a hack when I added pageable kernel support to CP67 when I was an undergraduate in the 60s. All of cp67 kernel started out fixed ... but I figured i could make lower-use stuff ... effectively "transient". I broke up pieces of the kernel into 4k, page-aligned "transient" executable chunks ... that could be brought in & out (using the standard paging mechanism). The cp67 flavor wasn't released in the product ... but something very similar was part of the standard vm370 product.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Evolution of Floating Point Newsgroups: alt.folklore.computers Date: Tue, 29 Sep 2009 23:05:22 -0400"Charlie Gibbs" <cgibbs@kltpzyxm.invalid> writes:
that was deployed at some number of internal locations ... and eventually morphed into workstation datasaves facility ... which was released as product ... then morphed into adsm ... and was moved to tivoli (when san jose was being unloaded) and is now called tsm.
i started out by taking vmfplc and modifying for much better density on 6250 tapes (vmfplc wasn't too bad on 800 or 1600) but wasn't as good for 6250. basicaly vmfplc dumped the file FST (file status) block as separate physical block and then started dumping file data blocks (as 4k records). For lots of "small" files ... the tape would be mostly gaps ... with FSTs (few tens of bytes each) as separate physical blocks with small data blocks. First modification I did was merged the FST into the same physical block(s) with the file data block. Cut the gaps in half for lots of small files. I then started out allowing file data records to be block up to 12k bytes. In all, it could double the effective amount that could get on the tape (especially for lots of small files).
tivoli storage manager:
http://www-01.ibm.com/software/tivoli/products/storage-mgr/
couple past posts mention vmfplc
https://www.garlic.com/~lynn/2003b.html#42 VMFPLC2 tape format
https://www.garlic.com/~lynn/2003b.html#43 VMFPLC2 tape format
I had some data from the univ. that had been on 800bpi tapes ... which i eventually moved to 1600bpi at the science center ... and then to 6250bpi at sjr (along with lots other stuff from the science center). Research then moved up the hill to almaden and 6250 tapes were replaced with 3480 cartridges (and data copied to 3480s).
recent post referencing almaden data center had period when apparently
random tapes were being mounted for "scratch" requests ... and valuable
data was lost (case where i had triple replicated on three different
tapes ... but all in the same tape library/data center)
https://www.garlic.com/~lynn/2009m.html#79 Existence of early 360 software ( was Re: Continous Systems Modelling Package)
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Wed, 30 Sep 2009 09:50:12 -0400jmfbahciv <jmfbahciv@aol> writes:
including incorporating "SPM" updates. "SPM" had originally been done for cp67 at Pisa (in italy). It allowed a virtual machine to set things up so that "messages" (sent to the virtual machine) could be "read" by software (running in the virtual machine).
other old email referring to converting my stuff from cp67 to vm370 base
for internal distribution (basically highly modified internal vm370
"product")
https://www.garlic.com/~lynn/2006v.html#email731212
https://www.garlic.com/~lynn/2006w.html#email750102
it was used for users being able to communicate with "services" running in service virtual machines (old name for things now called virtual appliances).
one of these service virtual machines was the networking application. "instant messages" had always been possible between users logged into the same cp67 system. "SPM" allowed a message to be sent to the network service virtual machine ... which carried instructions to forward the rest of the content to the network service virtual machine running somewhere else and then "messaged" to user on that machine.
later in the 70s, the author of rex(x) used the capability to implement distributed version of "space wars" (using special message to allow program to read incoming messages). A "space war" server was set up somewhere ... and people ran "space war" clients ... that managed the 3270 display and communicated with the "space war" server. If the server was on a different machine, the "clients" used the network service virtual machines to communicate with the "space war" server.
I had gotten blamed for computer conferencing on the internal network
in the late 70s and early 80s ... misc. past posts mentioning the
internal network
https://www.garlic.com/~lynn/subnetwork.html#internalnet
somewhat as a result, there was a researcher to study how i
communicated, including sitting in the back of my office for nine months
taking notes on how I communicated. They also got copies of all my
incoming & outgoing email and logs of all my instant messages (basically
my terminal was logged ... all input and output ... and then parsed for
incoming/outgoing instant messages). the result was also a stanford
phd thesis and material for some number of papers and books. misc.
past posts mentioning computer mediated conversation
https://www.garlic.com/~lynn/subnetwork.html#cmc
misc. past posts mentioning distributed "space war"
https://www.garlic.com/~lynn/2001f.html#10 5-player Spacewar?
https://www.garlic.com/~lynn/2003i.html#27 instant messaging
https://www.garlic.com/~lynn/2005e.html#64 Graphics on the IBM 2260?
https://www.garlic.com/~lynn/2006n.html#41 Tek 4010, info and prices
https://www.garlic.com/~lynn/2007l.html#44 internet game history
https://www.garlic.com/~lynn/2008c.html#2 folklore indeed
https://www.garlic.com/~lynn/2009j.html#79 Timeline: The evolution of online communities
misc. past posts mentioning virtual appliances
https://www.garlic.com/~lynn/2006t.html#46 To RISC or not to RISC
https://www.garlic.com/~lynn/2006w.html#25 To RISC or not to RISC
https://www.garlic.com/~lynn/2006x.html#8 vmshare
https://www.garlic.com/~lynn/2007i.html#36 John W. Backus, 82, Fortran developer, dies
https://www.garlic.com/~lynn/2007k.html#48 John W. Backus, 82, Fortran developer, dies
https://www.garlic.com/~lynn/2007m.html#67 Operating systems are old and busted
https://www.garlic.com/~lynn/2007m.html#70 Is Parallel Programming Just Too Hard?
https://www.garlic.com/~lynn/2007o.html#3 Hypervisors May Replace Operating Systems As King Of The Data Center
https://www.garlic.com/~lynn/2007s.html#4 Why do we think virtualization is new?
https://www.garlic.com/~lynn/2007u.html#39 New, 40+ yr old, direction in operating systems
https://www.garlic.com/~lynn/2007u.html#41 New, 40+ yr old, direction in operating systems
https://www.garlic.com/~lynn/2008.html#59 old internal network references
https://www.garlic.com/~lynn/2008b.html#52 China's Godson-2 processor takes center stage
https://www.garlic.com/~lynn/2008c.html#55 Kernels
https://www.garlic.com/~lynn/2008e.html#11 Kernels
https://www.garlic.com/~lynn/2008h.html#97 Is virtualization diminishing the importance of OS?
https://www.garlic.com/~lynn/2008l.html#14 recent mentions of 40+ yr old technology
https://www.garlic.com/~lynn/2008m.html#67 Is Virtualisation a Fad?
https://www.garlic.com/~lynn/2008m.html#68 New technology trends?
https://www.garlic.com/~lynn/2008n.html#57 VMware renders multitasking OSes redundant
https://www.garlic.com/~lynn/2008q.html#62 Virtualization: What is it exactly?
https://www.garlic.com/~lynn/2008s.html#56 Computer History Museum
https://www.garlic.com/~lynn/2009h.html#59 Operating Systems for Virtual Machines
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Opinions on the 'Unix Haters' Handbook'. Newsgroups: alt.folklore.computers Date: Wed, 30 Sep 2009 10:25:51 -0400Anne & Lynn Wheeler <lynn@garlic.com> writes:
recent reference to the ratings agencies
U.S. Ratings fraud continues
http://www.stockhouse.com/Community-News/2009/Sept/29/U-S--Ratings-fraud-continues
from above:
Most of the too-big-to-fail banks have actually been allowed to get
bigger. And ratings-fraud continues unabated with respect to the
so-called 'credit rating' agencies.
... snip ...
the congressional hearing from last fall into the rating agencies ... said that the seeds for this were sown in the early 70s when the rating agencies switched from the buyers paying for the ratings to the sellers paying for the agencies (creating the opening for conflict of interests ... i.e. producing the rating that the seller pays for).
somewhat related, IDC has item on their website that they bought the
"pricing services division" from one of the rating agencies in the early
70s (about the time, they switched from buyer paid ratings to seller
paid ratings). IDC was one of the early (virtual machine) online cp67
time-sharing service bureaus in the 60s ... and started fairly quickly
to move up the online value chain with lots of financial information.
disclaimer ... i interviewed with them in the 60s ... but didn't join.
misc. past references:
https://www.garlic.com/~lynn/2009.html#21 Banks to embrace virtualisation in 2009: survey
https://www.garlic.com/~lynn/2009.html#31 Banks to embrace virtualisation in 2009: survey
https://www.garlic.com/~lynn/2009.html#32 What are the challenges in risk analytics post financial crisis?
https://www.garlic.com/~lynn/2009.html#42 Lets play Blame Game...?
https://www.garlic.com/~lynn/2009.html#52 The Credit Crunch: Why it happened?
https://www.garlic.com/~lynn/2009.html#77 CROOKS and NANNIES: what would Boyd do?
https://www.garlic.com/~lynn/2009.html#79 The Credit Crunch: Why it happened?
https://www.garlic.com/~lynn/2009b.html#38 A great article was posted in another BI group: "To H*** with Business Intelligence: 40 Percent of Execs Trust Gut"
https://www.garlic.com/~lynn/2009b.html#49 US disaster, debts and bad financial management
https://www.garlic.com/~lynn/2009b.html#53 Credit & Risk Management ... go Simple ?
https://www.garlic.com/~lynn/2009b.html#78 How to defeat new telemarketing tactic
https://www.garlic.com/~lynn/2009c.html#1 Audit II: Two more scary words: Sarbanes-Oxley
https://www.garlic.com/~lynn/2009e.html#15 The background reasons of Credit Crunch
https://www.garlic.com/~lynn/2009e.html#30 Timeline: 40 years of OS milestones
https://www.garlic.com/~lynn/2009e.html#53 Are the "brightest minds in finance" finally onto something?
https://www.garlic.com/~lynn/2009e.html#70 When did "client server" become part of the language?
https://www.garlic.com/~lynn/2009f.html#41 On whom or what would you place the blame for the sub-prime crisis?
https://www.garlic.com/~lynn/2009f.html#49 Is the current downturn cyclic or systemic?
https://www.garlic.com/~lynn/2009g.html#27 Flawed Credit Ratings Reap Profits as Regulators Fail Investors
https://www.garlic.com/~lynn/2009h.html#40 Analysing risk, especially credit risk in Banks, which was a major reason for the current crisis
https://www.garlic.com/~lynn/2009n.html#20 UK issues Turning apology (and about time, too)
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Thu, 01 Oct 2009 10:23:18 -0400jmfbahciv <jmfbahciv@aol> writes:
mostly leased/dedicated ... but there were some dial. fairly early there was corporate requirement that (starting with computer-to-computer) links leaving corporate pysical premises had to be encrypted. there was comment circa 1985 that the internal network had over half of all the link encryptors in the world (some number of crypto companies were motivated by the business from the internal network).
in the 80s, as corporate was exposed to people having terminals at home and possibililty that executives having portable PCs ... there was requirement for encrypted PC communication. Corporation also instituted "dial-back" procedure for home terminal program ... dial-in, identify, hangup, and the system would dial-back your registered phone number. For emerging "road-warriers" ... corporation did custom encrypting 1200 baud modems (there would be dynamically generated random session key that was exchanged securily ... sort of an early version of "SSL").
slightly related posts mentioning getting involved with crypto
boxes
https://www.garlic.com/~lynn/2008h.html#87 New test attempt
https://www.garlic.com/~lynn/2008i.html#86 Own a piece of the crypto wars
https://www.garlic.com/~lynn/2009l.html#14 August 7, 1944: today is the 65th Anniversary of the Birth of the Computer
in effort I called HSDT (high-speed data transport)
https://www.garlic.com/~lynn/subnetwork.html#hsdt
doing HSDT effort also got us involved in some early NSFNET stuff (and
internal politics that prevented use from bidding on the NSFNET backbone
T1 RFP):
https://www.garlic.com/~lynn/subnetwork.html#nsfnet
misc. past posts mentioning internal network
https://www.garlic.com/~lynn/subnetwork.html#internalnet
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Status of Arpanet/Internet in 1976? Newsgroups: alt.folklore.computers Date: Thu, 01 Oct 2009 10:30:20 -0400jmfbahciv <jmfbahciv@aol> writes:
and when those leased lines with link encryptors ... between purely corporate sites ... also happened to cross national boundaries ... there was lots of interaction with gov. institutions around the world regarding whether it was allowed to have encrypted links that crossed national boundaries.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Sophisticated cybercrooks cracking bank security efforts Date: 1 Oct, 2009 Blog: Financial Crime Risk, Fraud and SecuritySophisticated cybercrooks cracking bank security efforts
from above:
Cybercrooks have stolen more than EUR300,000 in just three weeks from
German bank accounts using a sophisticated new Trojan that forges
online statements to hide the theft from victims.
... snip ...
also .....
Bank Trojan used against German accounts evades antifraud systems
http://searchfinancialsecurity.techtarget.com/news/article/0,289142,sid185_gci1369675,00.html?track=NL-102&ad=728247&asrc=EM_NLN_9397721&uid=1308899
It is possible to do digital signature authentication and hardware tokens w/o PKI. In the mid-90s, the banking industry looked at doing this and the PKI industry allowed that they would take the information from a financial institution and populate digital certificates with the information from account records at only $100/account.
The certificate-less issue was that the digital certificates were
actually redundant and superfluous since the financial institution
already had all the information in the account records. The rest of
the cost of deploying a digital signature infrastructure was on the
order of 5% of the what was being charged for digital certificates
(and it is actually possible to deploy a digital signature
infrastructure w/o digital certificates and/or PKI).
https://www.garlic.com/~lynn/subpubkey.html#certless
Some number of financial institutions with tens of millions of accounts were looking at billions (per annum) for digital certificates (which nominally had to be re-issued ever year).
The other issue with regard to financial "PKI" floundering in the mid-90s ... besides the enormous cost for something that was redundant and superfluous, had to do with the enormous payload bloat for payment transactions.
Appending (an enormously expensive, redundant and superfluous) digital
certificate on every payment transaction, typically increased the
payment transaction payload size by a factor of one hundred times.
https://www.garlic.com/~lynn/subpubkey.html#bloat
We were asked to come in to help word-smith the cal. state electronic signature legislation. There had been some factions lobbying for digital signatures and digital certificates as equivalent to "human signatures" (as well as non-repudiation) ... however the lawyers explained that digital signatures didn't satisfy the requirement for analogy to "human signatures".
There seemed to be possible semantic confusion because the terms "human signature" and "digital signature", both contained the word "signature".
There was even an suggestion floated (attempting to counteract the floundering PKI in the financial industry) ... that if banks & merchants were to pickup PKI operation, REG-E would be changed (for PKI payment transactions) to change the burden of proof from the institutions to the consumers ... and the consumers wold be convinced to pay for their own digital certificates.
Somebody raised the question, why would a consumer pay $100/annum for a (expensive, redundant and superfluous, and enormous payload bloat) digital certificate that would result in switching the burden of proof in payment transaction dispute from the institutions to the consumer.
In the cal. electronic signature legislation ... the lawyers did lay
out some of the requirements to be able to meet any "intent"
demonstration ... and/or demonstrating having read, understood,
agrees, approves, and/or authorizes.
https://www.garlic.com/~lynn/subpubkey.html#signature
... old copy of RFI response to NACHA for a (certificate-less) digital
signature operation ... using digital signatures purely for integrity
and authentication (eliminating much of spoofing, impersonation and/or
other trivial account fraud exploits)
https://www.garlic.com/~lynn/nacharfi.htm
and results here of the NACHA (certificate-less) digital signature
trials:
https://web.archive.org/web/20070706004855/http://internetcouncil.nacha.org/News/news.html
in that sense, the digital signature is the same as some recent cryptogram suggestions that uniquely establishes integrity of the transaction (hasn't been modified) and authentication of the sender.
this is basically what the x9a10 financial standard working group had
come up with in the mid-90s for x9.59 financial transaction standard
... some references
https://www.garlic.com/~lynn/x959.html#x959
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Real-Time Hackers Foil Two-Factor Security Date: 1 Oct, 2009 Blog: Financial Crime Risk, Fraud and SecurityReal-Time Hackers Foil Two-Factor Security
from above:
A forensic analysis performed later would reveal that an earlier visit
to another website had allowed a malicious program to invade his
computer. While the manager issued legitimate payments, the program
initiated 27 transactions to various bank account...
... snip ...
also ... little x-over
Internet crooks 'used virus to raid computer users' online bank
accounts'
http://www.dailymail.co.uk/sciencetech/article-1216930/Internet-crooks-used-virus-raid-users-online-bank-accounts.html?printingPage=true
This was an identified vulnerability/exploit identified by at least the mid-90s with regard to a compromised "end-point".
As mentioned in other discussions, the EU Finread standard in the 90s
had countermeasure for compromised PC by effectively moving the
end-point out to a hardened secure independent device. The device had
its own display and key pad and transaction processing. The
transaction was displayed and required physical action by human at the
independent keypad.
https://www.garlic.com/~lynn/subintegrity.html#finread
Any (compromised) PC then simply becames a store&forward transmission ... basically an intermediate point that could either forward or not forward the information .... possibly denial of service attack ... but in that respect ... not any different from any other intermediary transmission point at any place in the internet.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: lynn@GARLIC.COM (Anne & Lynn Wheeler) Subject: Re: IDCAMS delete with mask Newsgroups: bit.listserv.ibm-main Date: 1 Oct 2009 14:33:21 -0700John.McKown@HEALTHMARKETS.COM (McKown, John) writes:
recent reference to STL as example ... which in the early 80s they were
installing them on every floor in every tower ... basically in the
departmental "stock" room or in conference room.
https://www.garlic.com/~lynn/2009n.html#15 Mainframe Hall of Fame: Three New Members Added
another example is this old reference
https://www.garlic.com/~lynn/2001m.html#15 departmental servers
to customer initially looking at getting 20 4341s ... but order
grew to 210 4341s (over six month period):
https://www.garlic.com/~lynn/2001m.html#email790404b
43xx competed against vax in the entry and midrange market for customers
buying single or few number of machines (comparable number of sales)
... but 43xx were also sold in quantities to large customers ordering
multiple hundred at a time. this is vax sales sliced & diced by year,
model, US & non-US ... and it is easy to see that by mid-80s, that
market was moving to workstations & large PCs.
https://www.garlic.com/~lynn/2002f.html#0 Computers in Science Fiction
follow-on 4361/4381 anticipated to see equally large explosion in orders ... but by that time ... workstations & PCs were starting to move up the value chain and take over the entry & mid-range market segment (similar fate as what happened to vax).
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970
From: Anne & Lynn Wheeler <lynn@garlic.com> Subject: Re: Best IEFACTRT (off topic) Newsgroups: bit.listserv.ibm-main Date: Thu, 01 Oct 2009 18:38:51 -0400gerhard@VALLEY.NET (Gerhard Postpischil) writes:
4341 was nominally vanilla 370 (including 2k storage protect keys)
... with vm/370 ecps performance assist (carried over from 138/148)
... old post detailing what part of vm370 kernel was selected for ecps
microcode:
https://www.garlic.com/~lynn/94.html#21 370 ECPS VM microcode assist
in the 138/148 (and 4331/4341) ... it was vertical microcode engine that avg. about 10 microcode instructions per 370 instruction. ECPS managed to map approx. 1 (kernel) 370 instruction into each microcode instruction ... achieving effectively 10:1 speedup.
there was some look at doing something similar for MVS on 3033 ... and a somewhat similar, but large 3033 microcode package was done for MVS ... and newer MVS releases required the microcode package to run (compared to the vm370 ecps implementation which would run whether ecps was available or not). the issue with the high-end machines was that there was so much hardware optimization that 370 instruction was executing about as fast as microcode instruction ... so there was little speed-up going for one-for-one translation of 370 instruction to microcode (on high-end machines). the other part of the MVS package was dual-address space support ... attempting to address the problem with exploding size of common segment ... 16mbyte virtual address space per application, but kernel mapped to half that ... and common segment invented to preserve pointer-passing paradigm between applications and subsystems (now in different address space). for larger systems, common segment was starting to threaten exceeding five mbytes (reducing application space to only two mbytes).
In any case ... MVS was starting to look at the enormous explosion in 43xx (and vm370) installations (mentioned in "IDCAMS delete with mask" post) ... and there was some anticipation that MVS might be able to get some of that ... if MVS could be made to run on at least 4341 (no hope on 4331) ... but that required retrofitting the large 3033 MVS microcode change (including dual-address space support) to 4341.
it wasn't clear how it was justified ... considering the size of the effort and the expected number of incremental 43xx sales.
SHARE had already done a study that vm370 suffered via-s-vis vax/vms in the low-end and mid-range market because requiring more people hrs & skill level for care and feeding (i.e. both the 43xx and vax systems had dropped below some price threshold where people costs and people skill were starting to dominant). while vm370 skill/time wasn't quite as good as vax/vms ... it still was still way below what MVS required.
for topic drift ... using MVCK to test for dual-address space is
mentioned in this Amdahl patent
http://www.freepatentsonline.com/4979106.html
MVCK is also referenced in this IBM patent
http://www.freepatentsonline.com/5023773.html
There was a similar but different problem on 115/125 with MVCL. 360 instructions always checked operand starting and ending storage locations ... and if there was some problem, wouldn't execute the instruction. 370 introduced incrementally executing instructions (mvcl, clcl) where operand starting storage was checked ... but would incrementally execute the instruction ... checking the storage operand as it executed. If there was a problem ... the instruction would interrupt indicating how much had successfully executed.
I had a customer that wanted to run vm370 on (256kbyte) 125 (which hadn't been announced as officially supported) ... and I ran into the MVCL "bug". VM370 kernel build process had special sequence where it attempted to clear storage and determine how much (real) storage was available ... in single MVCL instruction (i.e. MVCL with 16mbyte length, clear up to end of real storage and then interrupt indicating end of real storage was located). However, the 125 MVCL would check ending address of storage operand and not even start execution ... which was taken as implying that there was zero real storage ... and vm370 kernel build would abort.
--
40+yrs virtualization experience (since Jan68), online at home since Mar1970